Plans supporting this feature: Enterprise
Before setting up Single Sign-On (SSO) between Document360 and Okta using the OpenID protocol, ensure you have administrative access to Okta. Please note that only users with Owner or Admin as Project role can configure SSO in Document360.
PRO TIP
It is recommended to open Document360 and Okta in two separate tabs/browser windows since configuring SSO in Document360 will require you to switch between Okta and Document360 multiple times.
Sign up for Okta
Access to an Okta account is required for configuring SSO with Document360. If you don't have an account:
Navigate to Okta Developer Sign-Up and complete the sign-up process.
Adding an Application in Okta
To create a Document360 SSO configuration using Okta, follow these steps:
Log in to Okta using your account credentials.
Switch to the admin user role by clicking on Admin at the top right next to your profile name.
From the left navigation list, expand the Applications dropdown and click Applications.
On the Applications page, click the Create App Integration button.
In the Create a new app integration popup, select OIDC - OpenID Connect as the Sign-in method and choose Web Application as the Application type, then click Next.
Document360 Service Provider (SP) Configuration
Next, you will need to configure Okta with the Service Provider (SP) details provided by Document360:
Open Document360 in a separate tab or panel.
Navigate to Settings > Users & permissions > SSO Configuration in Document360.
Click the Create SSO button.
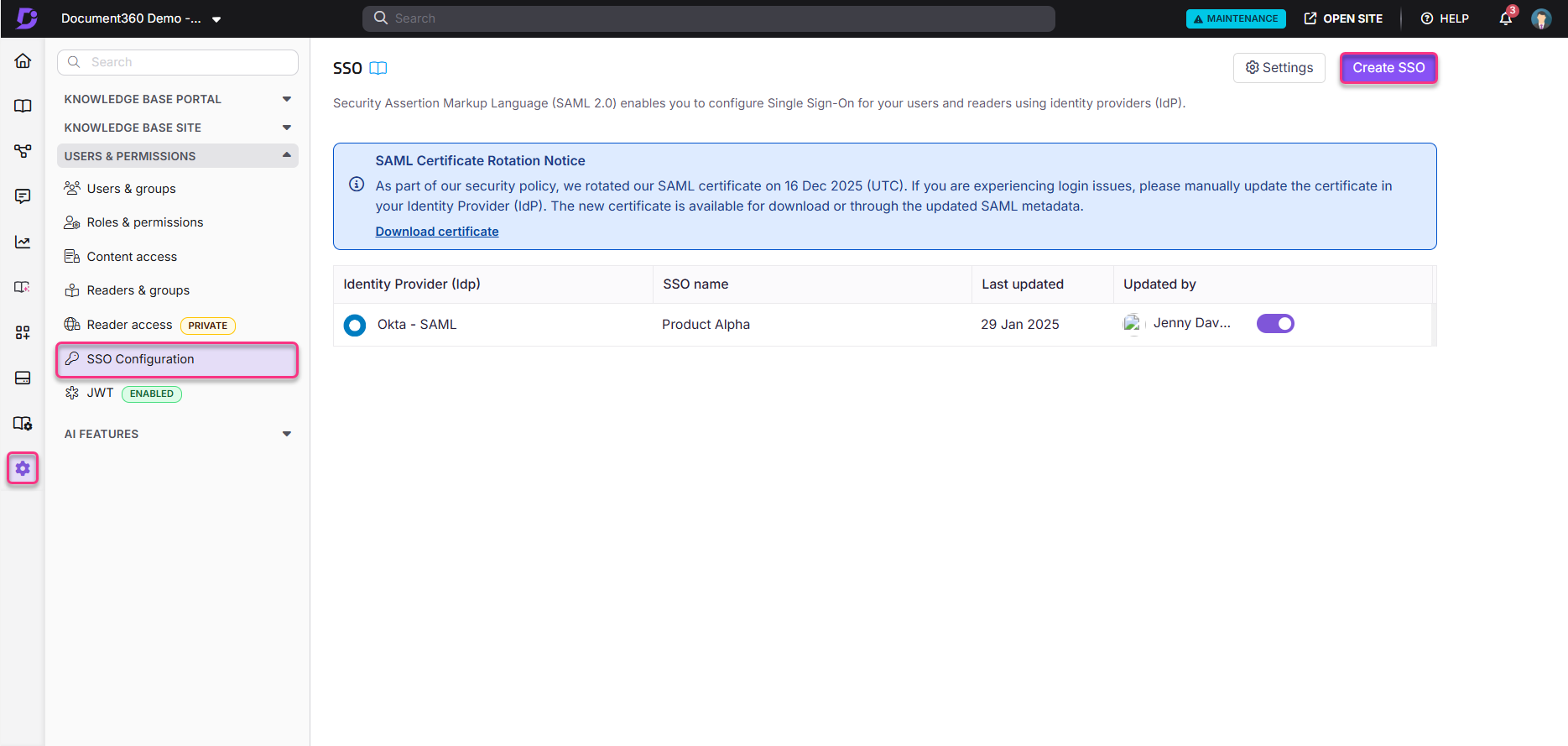
Select Okta as your identity provider to automatically navigate to the Configure the Service Provider (SP) page.
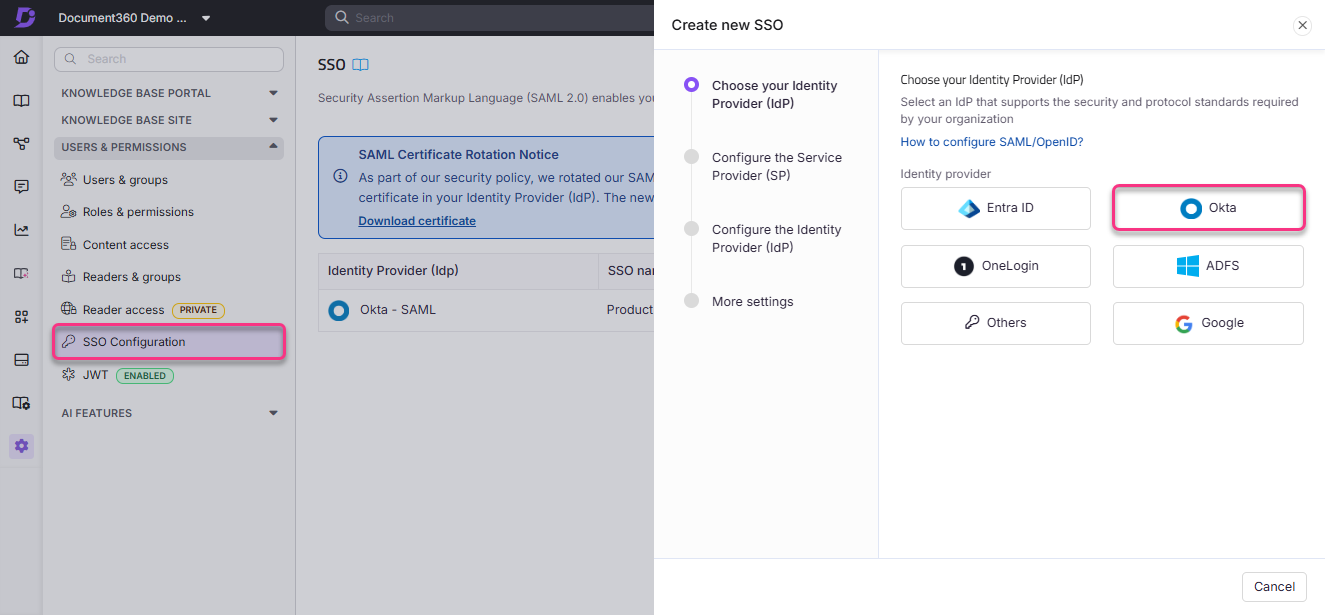
In the Configure the Service Provider (SP), select the OpenID radio button.
The Configure the Service Provider (SP) page contains the following values:
Subdomain name
Sign in redirect URI
Sign out redirect URI
In the New Web App Integration page on Okta:
Sign-in redirect URIs: Enter the Sign in redirect URI provided by Document360.
Sign-out redirect URIs: Enter the Sign out redirect URI provided by Document360.

Document360 OpenID SSO Configuration
Now, configure the SSO settings in Document360:
Return to the Document360 tab/panel displaying the Configure the Service Provider (SP) page.
Click Next to navigate to the Configure the Identity Provider (IdP) page and enter the corresponding values from your Okta configuration:
Okta | Document360 |
|---|---|
Client ID | Client ID |
Client Secret | Client Secret |
Issuer URI | Authority |
NOTE
To find the Issuer URI in Okta, navigate to Security > API.

Ensure that the Client ID and Client Secret match the values generated in Okta.
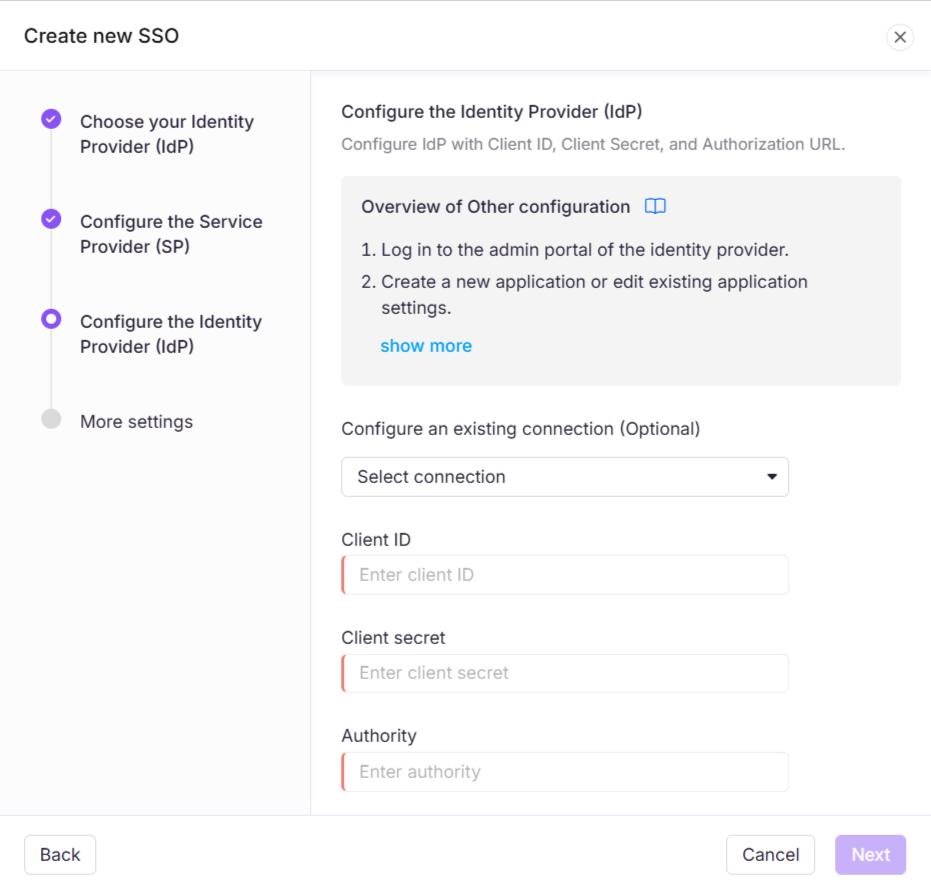
Toggle on/off the Allow IdP initiated sign in option based on your project needs.
Click Next to proceed to the More settings page.
More Settings
In the More settings page, configure the following:
SSO name: Enter a name for the SSO configuration.
Customize login button: Enter the text for the login button displayed to users.
Auto assign reader group: Toggle on/off as needed.
Sign out idle SSO user: Toggle on/off based on your requirements.
Choose whether to invite existing user and reader accounts to SSO.
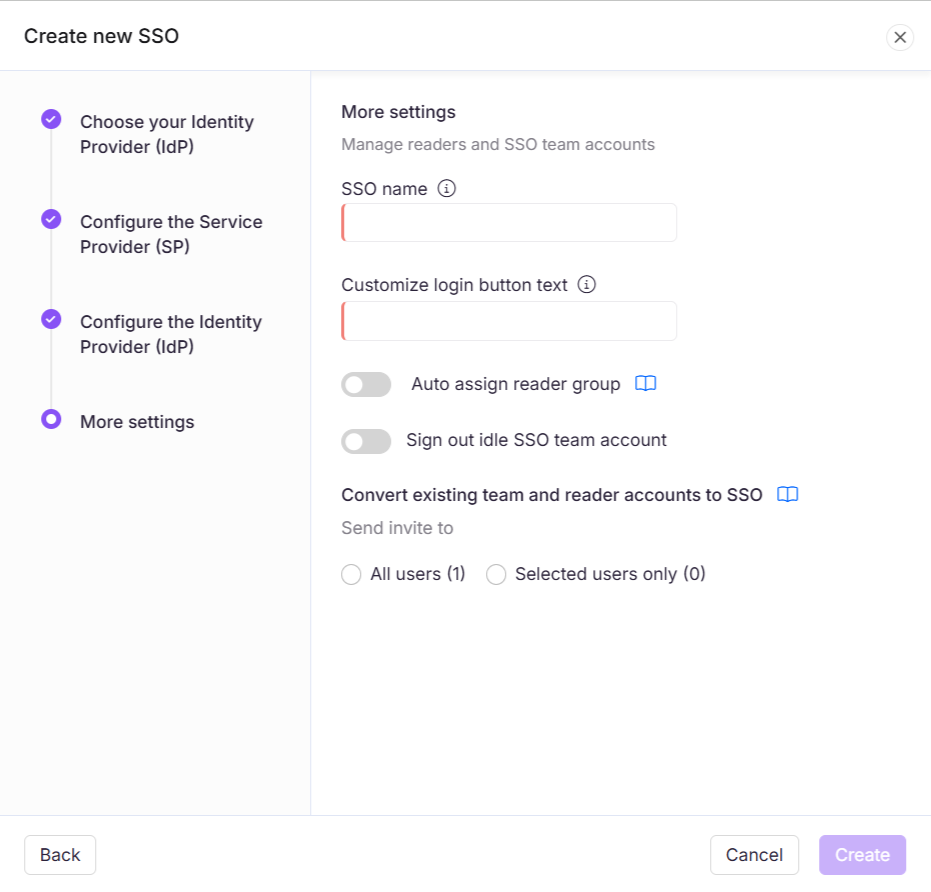
Click Create to complete the OpenID SSO configuration.