Plans supporting this feature: Professional Business Enterprise
At Document360, we are committed to transparency with our customers regarding our products and how we use AI to enhance your experience. Here is a comprehensive overview of Eddy AI's functionality, highlighting our robust security measures and privacy practice.
Compliance
Eddy AI, our advanced AI-powered tool, adheres to strict compliance standards such as:
GDPR: We adhere to the General Data Protection Regulation, ensuring robust data protection and privacy for all individuals in the European Union.
SOC 2 Type 2: Our practices align with the requirements of SOC 2 Type 2 and EU AI Act demonstrating our commitment to security, availability, and confidentiality.
NIST AI Risk Management Framework: Our practices are aligned with the NIST AI Risk Management Framework (AI RMF), a voluntary framework designed to improve the ability to incorporate trustworthiness considerations into the design, development, use, and evaluation of AI products, services, and systems.
Subprocessors
To deliver a high-quality service, Eddy AI leverages a network of trusted subprocessors. These include:
MongoDB: Used as our vector database.
OpenAI: Provides AI capabilities, utilizing their advanced models.
Azure: Our cloud provider ensures a scalable and reliable infrastructure.
Stripe: Facilitates secure payment processing.
Segment: Used for product analytics to enhance the user experience.
Mixpanel: Enables advanced analytics.
Data Security and Privacy
We take facts, safety, and privacy seriously. All facts associated with Eddy AI are securely stored and encrypted. Here’s how we ensure the integrity and confidentiality of your information:
Data at rest: All the information is encrypted using industry-standard encryption protocols.
Data in transit: Data transmitted between your tool and our servers is encrypted to save you from interception and tampering.
Eddy AI is designed to supply steady and dependable overall performance, even under high utilization. Document360 also provides an AI incident response plan.
Eddy AI data flow and secure connection to OpenAI
The diagram illustrates how customer queries, knowledge-base content, and metadata flow securely through Document360’s infrastructure before reaching OpenAI’s API. This provides complete transparency into how Customer Restricted Level (CRL) data is protected end to end. CRL is a list published by a Certificate Authority (CA) that contains digital certificates that are no longer valid before their expiration date. These certificates are revoked because they’re compromised, misused, incorrectly issued, or no longer trusted.
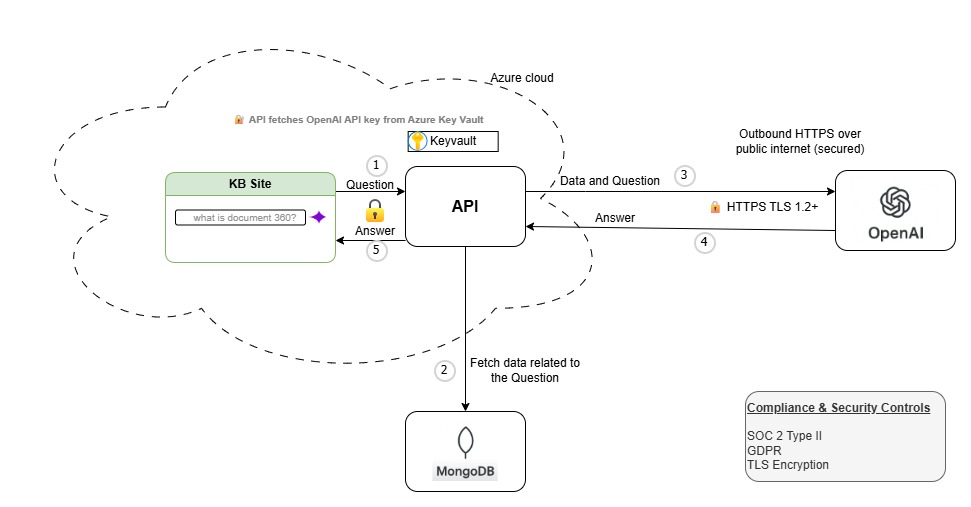
How the connection to OpenAI is secured
All requests to OpenAI’s API occur server-to-server from Document360’s backend.
All API keys required for communication with OpenAI are securely stored and retrieved from Azure Key Vault, as shown in the architecture.
CRL content is never exposed to the client browser during LLM processing.
TLS 1.2+ encryption secures all data in transit between Document360 and OpenAI.
CRL data is stored only within Document360’s systems (MongoDB cluster on Azure) and is never persisted by OpenAI.
As per the DPA with OpenAI, any data sent through their API is:
Not used for training
Retained for max 30 days, solely for abuse detection
Permanently deleted after the 30 days retention period
Flow summary
User submits a query inside Document360.
Query and retrieved KB snippets are processed inside Document360’s secure environment.
Only the minimum required text is sent to OpenAI via API, encrypted in transit.
OpenAI model returns the response to Document360 servers.
Document360 applies content filtering, grounding checks, and security policies.
The final answer is rendered to the user inside the Document360 UI.
This design ensures that:
CRL data never leaves controlled infrastructure except for minimal LLM processing
All external communication is encrypted and audited
Data exposure surface is extremely limited
Customers maintain full control and ownership of their content
Resources
1. Cryptography policy
Purpose: The policy aims to ensure the proper and effective use of cryptography to protect the confidentiality, authenticity, and integrity of information.
Scope: The policy applies to all information systems developed and/or controlled by Document360 that store or transmit confidential data.
Policy Owner: The CEO is responsible for the policy.
Effective Date: The policy becomes effective on March 1, 2024.
Risk Evaluation: Document360 evaluates risks and implements cryptographic controls to mitigate them where appropriate.
Encryption Standards: Strong cryptography with associated key management processes and procedures must be implemented and documented in accordance with industry standards, including NIST SP 800-57.
Key Management: Access to keys and secrets is tightly controlled, and there are specific recommendations for the usage of cryptographic keys, including key types, algorithms, and key lengths for various domains such as web certificates, web ciphers, and endpoint storage.
Exceptions: Requests for exceptions to the policy must be submitted to the CEO for approval and must be documented.
Violations & Enforcement: Known violations should be reported to the CEO and may result in disciplinary action, including termination of employment.
Data at Rest: Confidential data at rest must be encrypted using symmetric encryption with AES-256 bit for a maximum period of 1 year.
Passwords: Passwords must be hashed using one-way hash functions like Bcrypt, PBKDF2, scrypt, or Argon2, with a 256-bit key and a 10K stretch, including a unique cryptographic salt and pepper.
Vector Database Encryption: Text embeddings stored in MongoDB must use field-level encryption for vectors containing customer content.
Prompt & Response Encryption:
All user prompts must be encrypted before storage.
AI responses must be encrypted both in transit and at rest.
Third-Party Data in Transit:
TLS 1.3 is required for all OpenAI API calls.
Certificate pinning must be enforced for OpenAI endpoints.
Mutual TLS authentication is required for high-sensitivity deployments.
2. Incident response plan
Purpose and Scope: The document aims to provide a plan for managing information security incidents and events, covering all such occurrences within the company.
Definitions: It clarifies the difference between a security event (an observable occurrence relevant to data security) and a security incident (an event that results in loss or damage to data security).
Reporting and Documentation: Employees are instructed to report any suspected incidents immediately using specific communication channels, and all incidents must be documented.
Severity Levels: Incidents are categorized into S1 (Critical), S2 (High), and S3/S4 (Medium/Low) severity levels, with clear guidelines for escalation and response.
Incident Response Team: Engineer managers leads the incident response effort, with a designated "War Room" for centralized response. Regular meetings are held to update the incident ticket, document indicators of compromise, and perform other response activities.
Root Cause Analysis: For critical incidents, a root cause analysis is performed, documented, and reviewed by the Director of Engineering, who decides on the need for a post-mortem meeting.
Response Process: The response process includes triage, investigation, containment, eradication, recovery, and hardening, with a focus on lessons learned and long-term improvements.
Physical Security: The document addresses the physical security of affected systems, including isolation and backup procedures.
Breach Determination and Reporting: Only the Product Owner can determine if an incident constitutes a breach. The company shall promptly notify all relevant parties in accordance with policies and regulatory requirements.
External Communications: The company cooperates with customers, data controllers, and authorities as needed, with legal and executive staff determining the approach.
Roles and Responsibilities: The document outlines the specific responsibilities of incident responder roles.
Special Considerations: It includes handling internal issues, compromised communications, and root account compromises.
Incident Status and Summary: A detailed template is provided for documenting incident details, including date, time, location, personnel involved, type of information involved, indicators of compromise, root cause, and actions taken.
Policy Owner and Effective Date: The Product Owner is the policy owner, and the plan becomes effective on March 1, 2024.
AI-Specific Incident Categories:
S1 - Critical AI Incidents
Systematic bias affecting protected groups.
Successful jailbreak in production impacting more than 100 users.
PII exposed through AI-generated responses.
Sustained hallucination rate exceeding 5% for one or more hours.
S2 – High AI Incidents
Moderation API bypass detected.
Prompt injection attack impacting fewer than 100 users.
Model drift causing accuracy degradation of more than 10%.
Citation failure rate exceeding 15%.
S3 – Medium AI Incidents
Single instance of an unsourced AI response.
DAN-style jailbreak attempt that was successfully blocked.
Anomalous response latency exceeding 10 seconds.
3. Information security roles and responsibilities policy
Objective: To establish clear roles and responsibilities for protecting electronic information systems and related equipment.
Policy Owner and Effective Date: The CEO is the policy owner, and the plan becomes effective on March 1, 2024.
Applicability
Applies to all Document360 infrastructure, network segments, systems, employees, and contractors involved in security and IT functions.
Audience
All employees and contractors involved in the Information Security Program.
Includes partners, affiliates, temporary employees, trainees, guests, and volunteers.
Roles and Responsibilities
Executive Leadership:
Approves capital expenditures for security programs.
Oversees execution and communication of information security and privacy risk management.
Ensures compliance with laws and standards (e.g., GDPR, CCPA, SOC 2, ISO 27001).
Reviews vendor service contracts and oversees third-party risk management.
Director of Engineering:
Oversees information security in software development.
Implements and monitors security controls for development and IT processes.
Conducts IT risk assessments and communicates risks to leadership.
VP of Customer Support:
Manages information security tools and processes in customer environments.
Ensures compliance with data retention and deletion policies.
System Owners:
Maintain confidentiality, integrity, and availability of information systems.
Approve access and change requests for their systems.
Employees, Contractors, Temporary Workers:
Act responsibly to protect health, safety, and information resources.
Identify areas for improved risk management practices.
Report incidents and adhere to company policies.
Chief People Officer
Ensures employees and contractors are qualified and competent.
Oversees background checks, policy presentation, and Code of Conduct adherence.
Evaluates employee performance and provides security training.
Policy Compliance
Compliance measured through reports, audits, and feedback.
Exceptions must be pre-approved by the CEO.
Non-compliance can lead to disciplinary actions, including termination.
Document Control
Version: 1.0
Date: February 3, 2024
4. Secure development policy
Policy Owner and Effective Date: The CEO is the policy owner, and the plan becomes effective on March 1, 2024.
Purpose: To ensure that information security is designed and implemented within the development lifecycle for applications and information systems.
Scope: Applies to all Document360 applications and information systems that are business critical and/or process, store, or transmit Confidential data.
Secure-by-Design Principles:
Minimize attack surface area.
Establish secure defaults.
Apply the principle of Least Privilege.
Implement defense in depth.
Fail securely.
Avoid security by obscurity.
Keep security simple.
Privacy-by-Design Principles:
Proactive, preventative approach.
Privacy as the default setting.
Privacy embedded into design.
Full functionality without compromising privacy.
End-to-End Security.
Full lifecycle protection.
Development Environment: Logical or physical segregation of environments: Production, Test/Staging, Development.
System Acceptance Testing: Establish acceptance testing programs and criteria for new information systems, upgrades, and new versions. Complete a Release Checklist before deploying code.
Protection of Test Data: Test data must be selected carefully, protected, and controlled. Confidential customer data must be protected and not used for testing without explicit permission.
Change Control Procedures: Ensure development, testing, and deployment of changes are not performed by a single individual without approval and oversight.
Software Version Control: All software is version controlled, with access restricted based on role.
Policy Compliance: Measured through reports, audits, and feedback. Non-compliance may result in disciplinary action, up to and including termination.
5. Code of conduct policy
Policy Owner: The CEO is responsible for the policy.
Effective Date: The policy becomes effective on March 1, 2024.
Purpose: The policy aims to establish and maintain a safe and inclusive environment for all staff members.
Scope: This policy applies to all staff members across all professional settings within the organization.
Culture: The organizational culture promoted by this policy emphasizes respect, collaboration, and consideration among all employees.
Expected Behavior: Staff members are expected to actively participate in creating a respectful and collaborative workplace environment.
Unacceptable Behavior: Any form of harassment, violence, discrimination, or inappropriate conduct is strictly prohibited.
Weapons Policy: The policy prohibits the possession of weapons on company premises, with strict consequences for violations.
Consequences: Non-compliance with this policy will result in immediate corrective actions, including disciplinary measures and the requirement to report violations.
Responsibility: The CEO holds the responsibility for ensuring that all staff members adhere to and uphold the principles outlined in this policy.
6. Access control policy
Policy Owner: The CEO is responsible for the policy.
Effective Date: The policy becomes effective on March 1, 2024.
Purpose: The purpose of this policy is to restrict access to information and systems to authorized individuals in accordance with business objectives.
Scope: This policy applies to all systems operated by Document360 that handle confidential data for employees and external parties with network access.
Access Control and User Management Summary:
Identifying Users: Access privileges are allocated based on specific job roles and competencies required to perform tasks.
Maintaining Authorization: All allocations of privileged access are documented and maintained to ensure accountability.
Enforcing Security Measures: Multi-factor authentication (MFA) is mandatory for privileged access to enhance security. Generic administrative IDs are prohibited to prevent unauthorized usage.
Adopting Protocols: Time-bound access permissions are granted to limit exposure and reduce security risks.
Logging and Auditing: All privileged logins and activities are logged and audited to monitor for unauthorized access or misuse.
User Access Reviews: Regular reviews ensure that distinct and appropriate identities are maintained for those with privileged access.
Access Control Policy: Access is restricted to authorized parties only, ensuring that information remains protected.
Password Management: Secure log-on procedures and password policies are implemented to safeguard against unauthorized access.
User Access Provisioning: Access permissions are granted based on documented business requirements and validated needs.
Violations & Enforcement: Violations of this policy are reported and subject to enforcement measures to maintain compliance and security.
7. Data management policy
Policy Owner: The CEO is responsible for the policy.
Effective Date: The policy becomes effective on March 1, 2024.
Purpose: To ensure information is classified, protected, retained, and securely disposed of based on its importance to the organization.
Scope: Applies to all data, information, and information systems of Document360.
Data Classification: Confidential: Highly sensitive data needing the highest protection levels. Examples include customer data, PII, company financials, strategic plans, and technical reports.
Restricted: Proprietary information requiring thorough protection. Default classification for all company information unless otherwise stated. Examples include internal policies, legal documents, contracts, and emails.
Public: Information intended for public consumption and can be freely distributed. Examples include marketing materials and product descriptions.
Data Handling:
Confidential Data:
Restricted access to specific employees or departments.
Must be encrypted at rest and in transit.
Should not be stored on personal devices or removable media.
Requires secure storage and disposal.
Restricted Data:
Access restricted to users with a need-to-know basis.
Requires management approval for external transfer.
Secure storage and disposal are mandatory.
Public Data: No special protection or handling controls required.
Data Retention and Disposal:
Data retained as long as needed for business, regulatory, or contractual requirements.
Confidential and restricted data securely deleted when no longer needed.
PII deleted or de-identified when no longer needed for business purposes.
Annual Data Review: Management reviews data retention requirements annually to ensure compliance with the policy.
Legal Requirements: Data associated with legal holds or lawsuits is exempt from standard policy requirements and retained per legal counsel’s stipulations.
Policy Compliance: Compliance measured through business tool reports and audits.
Exceptions: Any exceptions to the policy require CEO approval.
Violations & Enforcement: Known policy violations should be reported to the CEO and can result in disciplinary actions, including termination of employment.
8. Operations security policy
Policy Owner: The CEO is responsible for the policy.
Effective Date: The policy becomes effective on March 1, 2024.
Purpose and Scope:
Ensure the secure operation of information processing systems and facilities.
Applies to all critical Document360 information systems and third-party entities with network access.
Documented Operating Procedures:
Technical and administrative procedures must be documented and accessible to relevant users.
Change Management:
Significant changes must be documented, tested, reviewed, and approved before deployment.
Emergency changes require retrospective review and authorization.
Capacity Management:
Monitor and adjust processing resources and system storage to meet performance requirements.
Include human resource capacity in planning and annual risk assessments.
Data Leakage Prevention:
Identify and classify information per the Data Management Policy.
Train users on proper handling of sensitive information.
Use Data Loss Prevention (DLP) tools based on risk assessment.
Web Filtering:
Implement DNS and IP blocking to restrict access to risky websites.
Block websites with malicious content or command and control servers unless necessary for business.
Separation of Environments:
Strictly segregate development, staging, and production environments.
Do not use confidential production customer data in development or test environments without approval.
Systems and Network Configuration:
Follow configuration and hardening standards to maintain system and network security.
Review production network access configuration rules annually.
Protection from Malware:
Implement detection, prevention, and recovery controls for malware.
Utilize anti-malware and threat detection software on all company endpoints and emails.
Information Backup: Design and implement backup processes for systems and data, ensuring customer data recovery per SLAs.
Logging and Monitoring: Implement logging and monitoring to detect and respond to security incidents.
Control of Operational Software: Manage the installation and use of operational software according to established rules.
Threat Intelligence: Collect and analyze information security threats to produce actionable intelligence.
Technical Vulnerability Management: Identify, assess, and address technical vulnerabilities in a timely manner.
Restrictions on Software Installation: Establish rules for software installation to ensure security and compliance.
Information Systems Audit Considerations: Plan and agree on audit requirements to minimize disruptions to business processes.
Systems Security Assessment and Requirements: Include security requirements in the acquisition or significant changes to systems.
Data Masking: Implement data masking techniques to protect PII and sensitive data based on risk assessment.
9. Data retention policy
Policy Owner: The CEO is responsible for the Data Retention Policy.
Effective Date: The policy becomes effective on March 1, 2024.
Purpose: This policy outlines how data is stored, analyzed, and deleted within Document360, ensuring transparency and user control over retained information.
Scope: This policy applies to all customers using Document360, including both public and private knowledge base projects.
Data Collection:
For public sites: No user-level data is collected.
For private projects: We collect user-level data including the identity of the user submitting a prompt, timestamps, and other user information available within Document360.
Data Usage: Document360 stores all prompts/questions entered in the Eddy AI Chatbot to perform the following analyses:
Topical Analysis: Clustering of questions/prompts using in-house algorithms and OpenAI APIs.
Citation Analysis: Identifying the most cited articles.
Metrics: Displaying depth metrics and tracking answered vs. unanswered questions.
Customization: This policy is not customizable by the customer, but customers have the right to request deletion of their data at any time during the contract period.
Data Retention and Deletion:
All collected data is retained within your Document360 project.
Data is permanently deleted when the knowledge base project is deleted.
You may request deletion of this data at any point during your contract with Document360.
Responsibility: The CEO is responsible for ensuring the implementation and compliance of this policy across all customer accounts and projects.
10. AI Risk Assessment and Management Policy
Policy Owner: Senior Director – Data Science.
Effective Date: The policy becomes effective on January 1, 2025.
Purpose: To establish a systematic approach for identifying, assessing, prioritizing, and managing risks associated with Eddy AI across its entire lifecycle.
Key Components:
Initial AI Impact Assessment: A pre-development assessment must be completed prior to any development activity, covering intended use cases, potential harms, risk likelihood and impact, stakeholder identification, and mitigation strategies.
Ongoing Risk Monitoring: Risks are reviewed on a quarterly basis, with comprehensive assessments conducted annually.
Risk Tolerance Thresholds: Risks are classified into four categories: unacceptable risks (deployment prohibited), high risks (enhanced controls required), medium risks (standard controls applied), and low risks (monitoring only).
Risk Register: A centralized documentation of all identified risks, mitigation measures, residual risks, and designated ownership.
11. AI Fairness and Bias Management Policy
Policy Owner: Senior Director – Data Science
Effective Date: The policy becomes effective on January 1, 2025.
Purpose: To identify, measure, mitigate, and continuously monitor bias within Eddy AI systems, ensuring fair and equitable treatment across all user groups and content types.
Bias Categories:
Systemic Bias: Bias originating from third-party large language models (LLMs).
Computational/Statistical Bias: Bias arising from algorithmic design choices, data sampling methods, or the mathematical properties of the underlying models.
Human-Cognitive Bias: Bias introduced through human assumptions, perceptions, and decision-making processes.
Bias Testing Requirements:
Pre-Deployment
Content Representativeness Analysis: Analyse the knowledge base to evaluate topic balance, depth, and diversity of perspectives.
Stereotype Testing: Test the system using queries related to protected characteristics and verify that the AI consistently refuses to reinforce stereotypes.
Language Fairness: For multilingual knowledge bases, measure and compare response quality across all supported languages.
Post-Deployment Monitoring
Monthly: Conduct unanswered question analysis segmented by topic or user group.
Quarterly: Perform a full bias audit using an updated test corpus to assess.
Annually: Engage an external auditor to conduct an independent bias review and publish a transparency report.
Data privacy
We prioritize your privateness and cling to strict information dealing with practices:
Data Privacy Compliance: We have signed a Data Processing Agreement (DPA) with OpenAI, outlining our commitment to data privacy and protection. For more details, refer to DPA with OpenAI.
We use OpenAI’s ChatGPT-4.1 Mini and GPT-4o models to power Eddy AI, delivering cutting-edge performance and capabilities.
This feature adheres to OpenAI's privacy policies by using a form of OpenAI integration.
We send data to OpenAI via their APIs. An extract from the policy states, "OpenAI will not use data submitted by customers via our API to train OpenAI models or improve OpenAI's service offerings." Any data sent through the API to OpenAI will be retained for analytical purposes for a maximum of 30 days, after which it will be deleted.
NOTE
Read the complete OpenAI API data usage policies.
If you have any queries regarding Document360's data policy, please read our Privacy policy.
OWASP
The Open Worldwide Application Security Project (OWASP) is a globally recognized nonprofit organization dedicated to improving software security. OWASP provides free, open-source resources, tools, and community-driven projects that help organizations identify, manage, and mitigate security risks. One of their well-known initiatives is the publication of "Top 10" lists that spotlight the most critical security vulnerabilities in diverse domains.
OWASP’s top 10 threats for Large Language Model (LLM) applications
As AI technologies evolve, OWASP has extended its expertise to Large Language Model applications, identifying the top 10 security risks unique to these systems:
1. Prompt Injection: Malicious inputs designed to manipulate or hijack the LLM’s response behavior.
2. Insecure Output Handling: Failure to properly sanitize or validate LLM outputs, leading to security vulnerabilities downstream.
3. Training Data Poisoning: Corrupting training datasets to sabotage or covertly control model behavior.
4. Model Denial of Service: Attempts to exhaust LLM computational resources, causing downtime or degraded performance.
5. Supply Chain Vulnerabilities: Risk introduced via third-party datasets, pre-trained models, or plugins.
6. Sensitive Information Disclosure: Unintended leaking of confidential or personal data in model outputs.
7. Insecure Plugin Design: Plugins lacking proper validation or access controls, exposing attack surfaces.
8. Excessive Agency: Over-empowering LLMs, possibly leading to unintended or harmful autonomous actions.
9. Overreliance: Blind trust in LLM outputs without human validation, risking misinformation or poor decisions.
10. Model Theft: Unauthorized replication or extraction of proprietary LLM models.
Addressing key OWASP top 10 threats for Ask Eddy
Within Ask Eddy’s AI-driven service, several OWASP LLM threats are prioritized and addressed with targeted controls:
LLM01: Prompt Injection
We validate the inputs before passing it for further processing. We isolate context from prompts. Also, our systems instructions are strengthened to address prompt injection attacks. Eddy AI will only produce response based on your knowledge base content. We use moderation API to detect and flag malicious prompts.
LLM04: Data and Model Poisoning (Embeddings)
We do not have LLM on our own. We rely on OpenAI APIs for creating text embeddings. Based on the DPA we executed with OpenAI, OpenAI employs robust techniques against data and model poisoning.
LLM05: Improper Output Handling
We do not use tool calling in our architecture. All data are stored securely in MongoDB cluster as per our SOC II compliance and GDPR practices. We use state-of-the-art encryption to protect data at rest and transit.
LLM08: Vector and Embedding Weaknesses
We use OpenAI APIs for embeddings and securely stored against your content. We create embeddings based on your knowledge base content. Thus, embeddings cannot be manipulated or poisoned by external content sources. When the content is updated/modified, corresponding text embeddings are also updated.
LLM09: Misinformation
We have stringent system instructions in place to avoid proving false information. If LLM decide that it cannot produce a confident response, it will say "I do not know". We use latest GPT model 4.1 mini that is less prone to hallucination.
Processes and accountability for continuous monitoring
To effectively manage these risks, Ask Eddy employs the following governance and monitoring structures:
Automated Threat Detection: Real-time monitoring systems that flag unusual input patterns or suspicious model behavior.
Audit Trails: Comprehensive logging of input-output interactions for forensic analysis and compliance verification.
Incident Response Protocols: Defined workflows for rapid containment, assessment, and remediation of security events.
Compliance Alignment: Regular audits and updates aligned with frameworks such as SOC 2, GDPR.
By integrating these security principles and best practices, Ask Eddy ensures a resilient, trustworthy AI service aligned with OWASP’s recommendations.
Commitment to security and OWASP best practices
Document360 prioritizes security as a fundamental aspect of its knowledge management platform. Recognizing OWASP as the global authority on software security, Document360 aligns its security practices and guidance with OWASP’s widely adopted standards, including the OWASP Top 10 application security risks and the emerging OWASP LLM Top 10 for AI-driven applications.
Integration of OWASP principles
Document360 incorporates OWASP principles by:
Embedding secure coding and input validation best practices inspired by OWASP guidelines into its development lifecycle.
Ensuring that common vulnerabilities highlighted by OWASP, such as injection flaws and insecure direct object references, are mitigated through robust platform architecture.
Leveraging OWASP’s AI and LLM-specific risk frameworks to safeguard integrations and AI-powered features within Document360.
Providing secure API access with authenticated tokens, protecting data flow consistent with OWASP recommended controls.
Alignment with Industry Security Standards
Document360 complements OWASP’s security focus by adhering to additional frameworks and certifications:
Hosting on Microsoft Azure Cloud platform with advanced security protections including DDoS defense and encrypted data storage.
Compliance with GDPR, SOC 2 Type II and other relevant regulations and standards.
Continuous monitoring and automated threat detection aligned with OWASP’s Security Logging and Monitoring recommendations.
Learn more about OWASP and how Document360’s security strategy aligns with best practices:
OWASP Official Site: https://owasp.org
OWASP Top 10 Project: https://www.owasptopten.org
Document360 Security Overview: https://docs.document360.com/docs/security
Safety testing & defenses
Moderation API
What it is: An automated safety filter that screens inputs and model outputs for violent, sexual, hateful, self-harm, and other policy-restricted content.
How we use it: We call the Moderation API on user prompts and candidate responses. If content is flagged, Eddy AI blocks, redacts, or routes to safe fallback copy. All blocked user prompts are logged for review.
Customer impact: Reduces the risk of unsafe responses and helps you enforce acceptable-use policies across your knowledge base.
Operational controls
Pre-prompt and post-response moderation on all interactive surfaces.
Severity tags in logs for compliance review.
Periodic threshold tuning to balance recall vs. false positives.
“DAN”-style jailbreak testing
What it is: “DAN” (Do-Anything-Now) is a well-known jailbreak pattern that tries to coerce an LLM to ignore instructions, policies, or permissions. We treat “DAN” as shorthand for a class of prompt-engineering attacks (role-play coercion, policy override requests, nested instruction payloads).
How we use it: We maintain a corpus of DAN-style and related jailbreak prompts and run them against staging environments as part of our red teaming practice. We harden system prompts, isolate retrieved context, and verify that the model refuses to act outside scope.
Customer impact: Strengthens resistance to instruction override so responses remain grounded in your authorized content and policies.
Operational controls
Regular replay of jailbreak test sets (including DAN variants) during releases.
Guardrail rules that nullify “ignore previous instructions” and similar coercion clauses.
Automated alerts on any successful jailbreak in pre-prod; deploy blocked until fixed.
NOTE
We do not endorse or enable any “DAN mode.” References to DAN here are solely about defensive testing against jailbreak attempts.
Adversarial testing
What it is: Structured attempts to break or degrade the system using hostile inputs (token stuffing, prompt injections, context contamination, unicode/encoding tricks, logit attacks, denial-of-wallet prompts).
How we use it: We run continuous adversarial tests across the RAG pipeline (retrieval, ranking, grounding, and response). Tests include injection strings in user prompts and in KB content to validate isolation and output sanitation.
Customer impact: Improves robustness against manipulation, reduces hallucination risk, and protects latency/cost under abuse.
Operational controls
Scheduled adversarial test runs per release; additional runs after major model or prompt updates.
Metrics tracked: jailbreak success rate, injection pass-through rate, grounded-answer rate, refusal accuracy, latency/compute spike alerts.
Findings feed back into prompt policies, retriever filters, and content sanitizers.
FAQ
Does Document360 involve any generative AI or large language model (LLM) features?
Yes, Eddy AI, a feature in Document360, uses third party LLMs such as OpenAI and generative AI to enhance the user experience. It leverages advanced language models to provide smart assistance and content generation.
Can we choose not to train third-party AI/LLMs on our data?
Yes, customer data is not used to train AI/LLM models. Eddy AI uses OpenAI’s technology, but as per OpenAI’s privacy policy and our agreement with them, any data sent through their system is not used for AI training.
We send data to OpenAI through their API. As stated in their policy: "OpenAI will not use data submitted by customers via our API to train OpenAI models or improve OpenAI's service offerings." However, OpenAI may retain the data for up to 30 days for analysis and compliance purposes, after which it is permanently deleted.
Is Eddy AI built on the same infrastructure as Document360?
Yes, Eddy AI runs on the same secure and reliable infrastructure as Document360. This ensures consistent performance and compliance with our standards.
What countries and regions are these AI technologies/platforms/models hosted?
The AI technologies/platforms/models are hosted in the European Union (EU) region.
How does Document360 ensure that my data is not accessed or leaked to other customers? What security assurance is approved?
Document360 is SOC II compliant and adheres to industry-standard engineering best practices to ensure data isolation and protection. Robust security measures are implemented to prevent unauthorized access, ensuring that your data remains secure and inaccessible to other customers. For more details, refer to our Security practices.
How does Document360 ensure that non-targeted customer data is not ingested?
Document360 strictly adheres to the GDPR and the EU AI Act. Our internal processes and data handling practices are designed to align with all relevant legal and compliance requirements, ensuring that only intended and authorized data elements are processed. Non-targeted customer data is explicitly excluded from ingestion.
What is the uptime SLA, and is it supported by all subprocessors and third parties?
Document360 maintains a 99.99% uptime SLA, which is fully supported by all relevant subprocessors and third-party service providers involved in delivering our services.
What controls are in place to detect and prevent errors?
We log all outputs and responses generated by Eddy AI. In addition, we are in the process of integrating LLM observability tools to enhance monitoring and error prevention capabilities.
What is the expected margin of error for Eddy AI responses? How is adherence to the permitted error margin monitored and measured?
Based on our internal testing, Eddy AI demonstrates an accuracy rate of 96–98% when responding to user queries. We are actively integrating LLM observability tools and use evaluation frameworks such as OpenAI Evals, RAGAS, and GeneralQA metrics to assess performance and accuracy against defined benchmarks.
Has the product been assessed for bias, toxicity, or harmful content such as threats, profanity, or political polarity?
Yes, we use OpenAI Moderation APIs to evaluate responses for harmful content. If a response is flagged, Eddy AI will either avoid generating the response.
How is the risk of AI hallucination managed in Eddy AI?
Document360 has an AI risk mitigation strategy. Eddy AI is strictly constrained to your knowledge base content. Our system prompts guide the AI to avoid generating unsupported or cooked up responses. If Eddy AI is unsure or cannot cite a reliable source, it will respond with “I do not know.”
Are AI decisions explainable, and is there human oversight in the process?
Yes, all AI-generated responses from Eddy AI include inline citations, allowing end users to clearly see the source of the information and understand how the response is generated. Additionally, we follow a human-in-the-loop approach as part of our AI governance. While Eddy AI can assist with recommendations, final decisions are left to humans, ensuring oversight and accountability.
How do you ensure that sensitive or confidential data are not exposed to other clients?
We have a DPA signed with OpenAI stating that data will not be used for training or shared with others. We are SOC2 Type II and GDPR compliant. The data shared with AI is limited to the individual user's access permissions and not the entire project.
How is the confidentiality of my data maintained, and are any human reviewers involved in processing it?
All project data is encrypted at rest, and all data sent to the AI model is encrypted in transit. We use AES 256-bit encryption for data at rest and HTTPS with TLS 1.2 for data in transit. No human reviewers read, annotate, or process your data, and we do not train our own LLMs.
Are the data anonymized before being processed by the AI models?
Yes, we run internal processes to detect any personally identifiable information (PII). If PII is detected, it is masked and replaced with placeholders before sending the data to any third-party models.
How do you ensure transparency and identify biases? How do the AI models generate responses?
We use OpenAI’s LLMs and rely on their scorecards and reports for transparency. We follow red teaming best practices to identify biases and periodically test for model drift. For generating responses, we use a Retrieval Augmented Generation (RAG) approach, where context is retrieved from our knowledge base and sent to the LLM.
What steps are taken to ensure the reliability and performance of your AI models?
We offer a 99.96% uptime SLA and are working on integrating a backup LLM provider. We regularly monitor for anomalies using red teaming practices, model drift tests, and evaluations that track parameters like accuracy and context recall. If undesirable behavior is detected, we investigate the root cause and may adjust system prompts, upgrade to a new LLM, or suggest content changes to customers.
How do you manage model updates and ensure ongoing performance?
We regularly run evaluations to monitor performance and model drift. Based on the results, we update our systems and adopt newer LLMs to improve performance and accuracy.