Plans supporting this feature: Enterprise
OpenID Connect (OIDC) is an open standard authentication protocol that allows users to log in to multiple web-based applications using a single set of credentials. It's built on top of the OAuth 2.0 authorization framework. With OpenID enabled, Document360 users can log in to the platform using their existing credentials from an identity provider (IdP). This eliminates the need for users to remember multiple passwords and reduces the risk of unauthorized access. Document360 supports the configuration of multiple single sign-on (SSO) endpoints, allowing both users and readers to log in using their preferred identity provider.
Supported identity providers
Document360 supports the following identity providers (IdP):
Okta
Entra ID
Google
Auth0
ADFS
OneLogin
Others
Configuring SSO using OpenID
Log in to your Document360 account and navigate to your desired project.
Navigate to Settings () > Users & permissions > SSO Configuration.
Click Create SSO.
Select an identity provider from the Choose your Identity Provider (IdP) page.
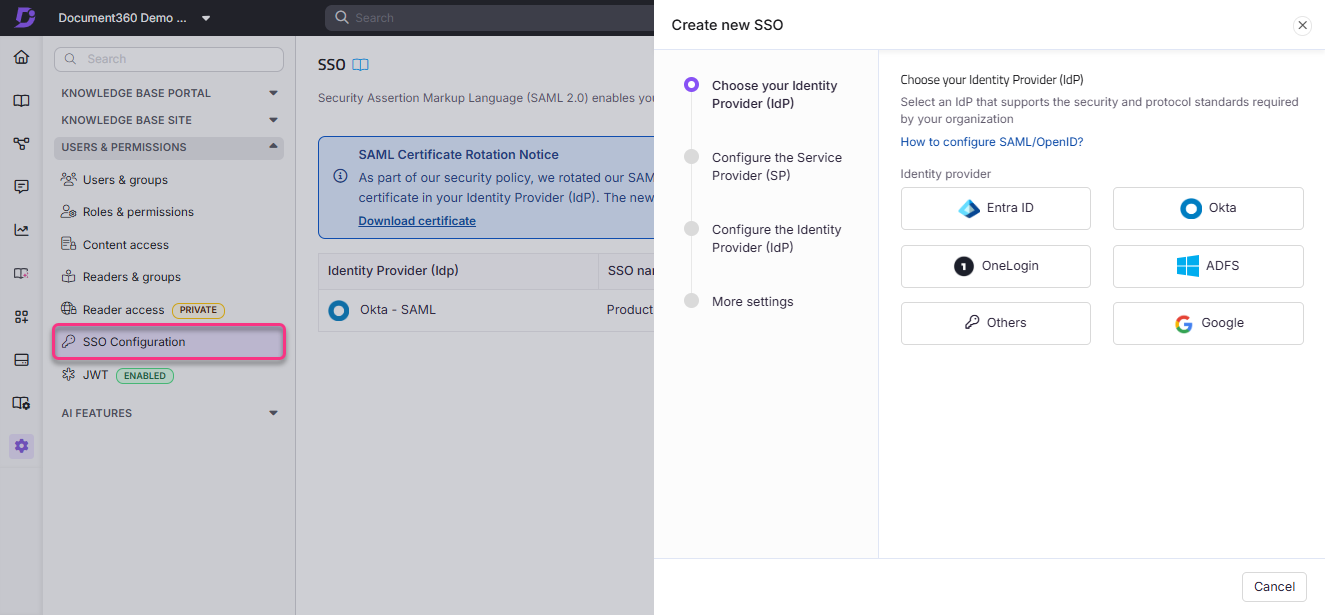
Select OpenID from the Configure the Service Provider (SP) page.
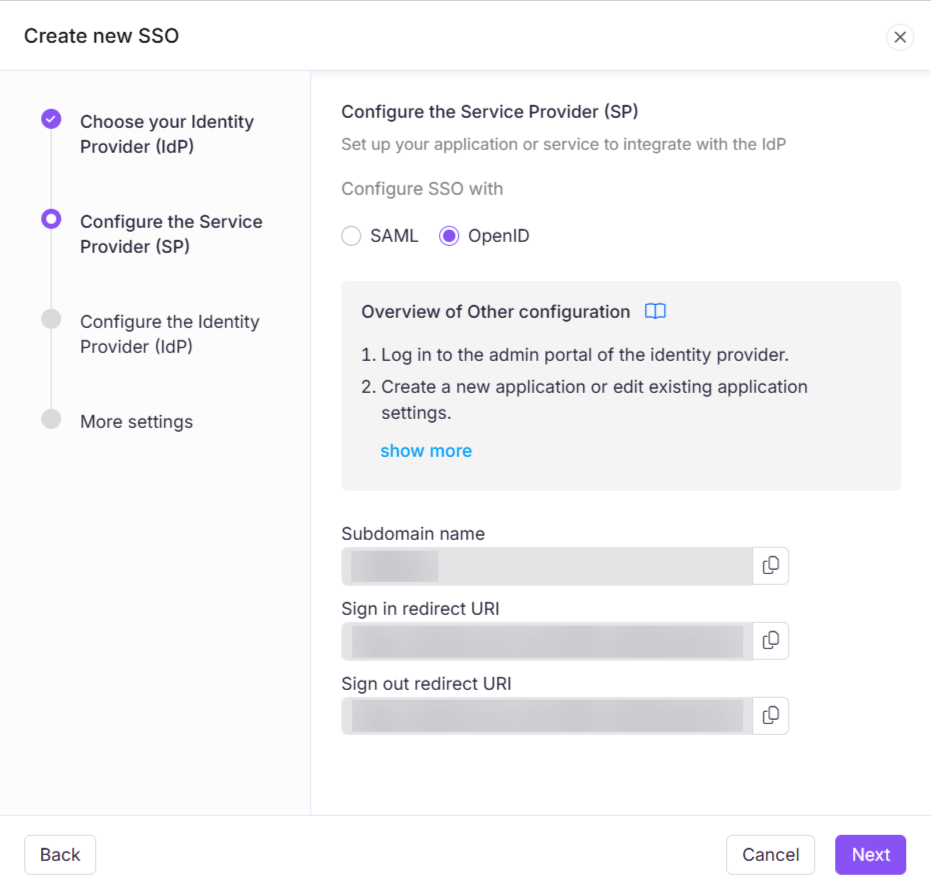
Using the details provided in the Configure the Service Provider (SP) page, configure the Document360 application with the previously selected identity provider.
Using the details provided by the identity provider, setup the SSO configuration in Document360 on the Configure the Identity Provider (IdP) page.
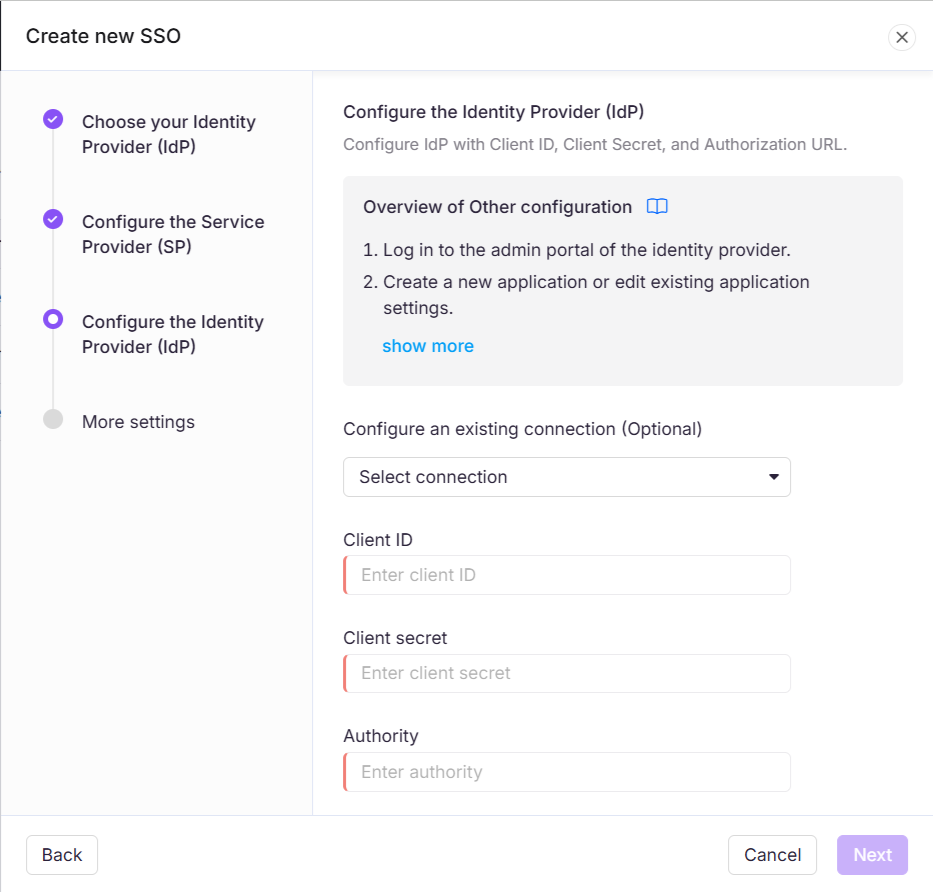
Once you have successfully completed the SSO configuration based on the OpenID protocol, you can invite members from your project to the configured SSO application.
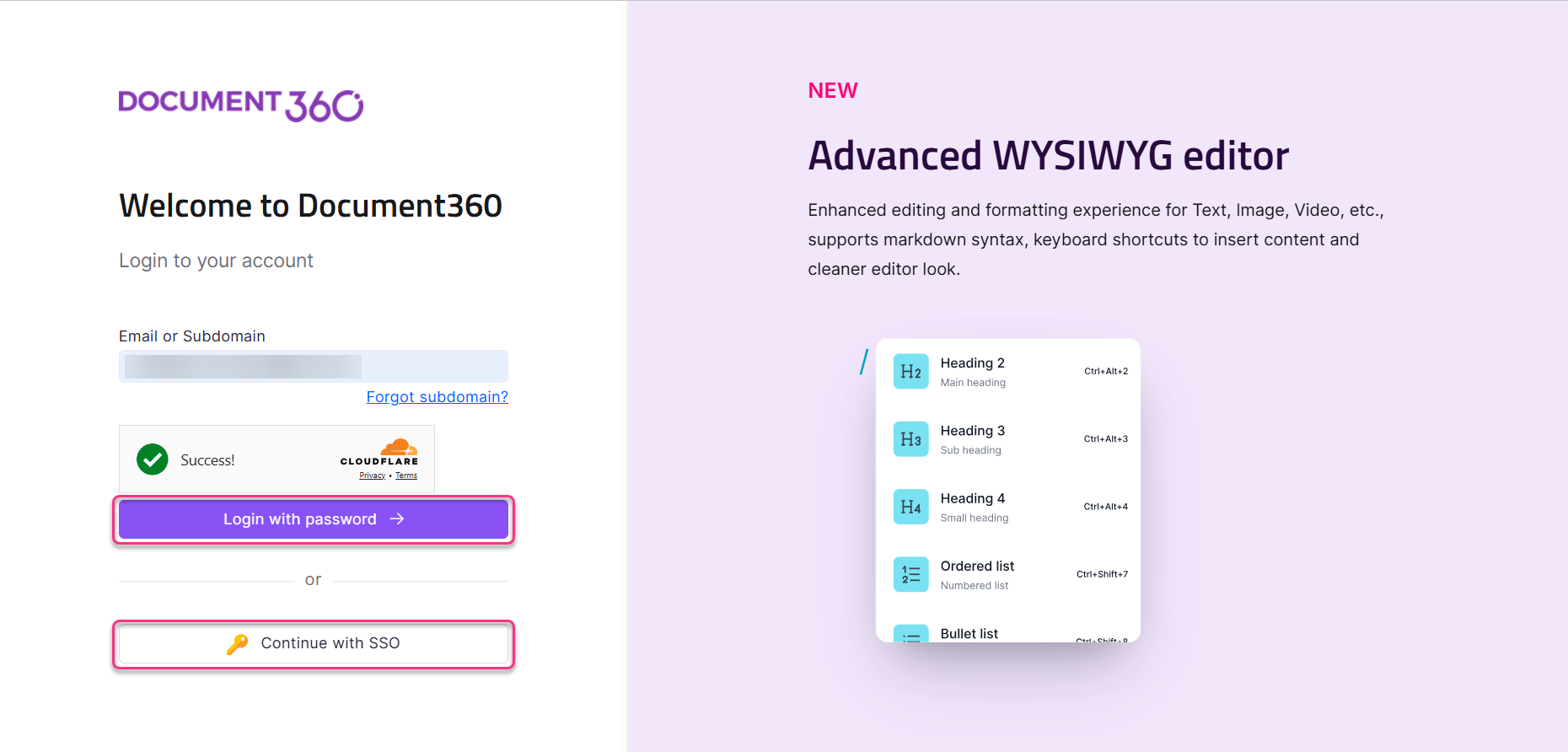
Now, users can login to Document360 either using their email and password or using SSO.
Troubleshooting
If you encounter issues during the OpenID SSO setup or login, refer to the following common errors and their solutions:
Authority URL configuration error
Error: IDX20803: Unable to obtain configuration from: 'System.String'
This error typically occurs due to an incorrect or misconfigured Authority URL in the OpenID SSO configuration.
Steps to resolve:
To resolve this issue,
Identify the Correct Authority URL
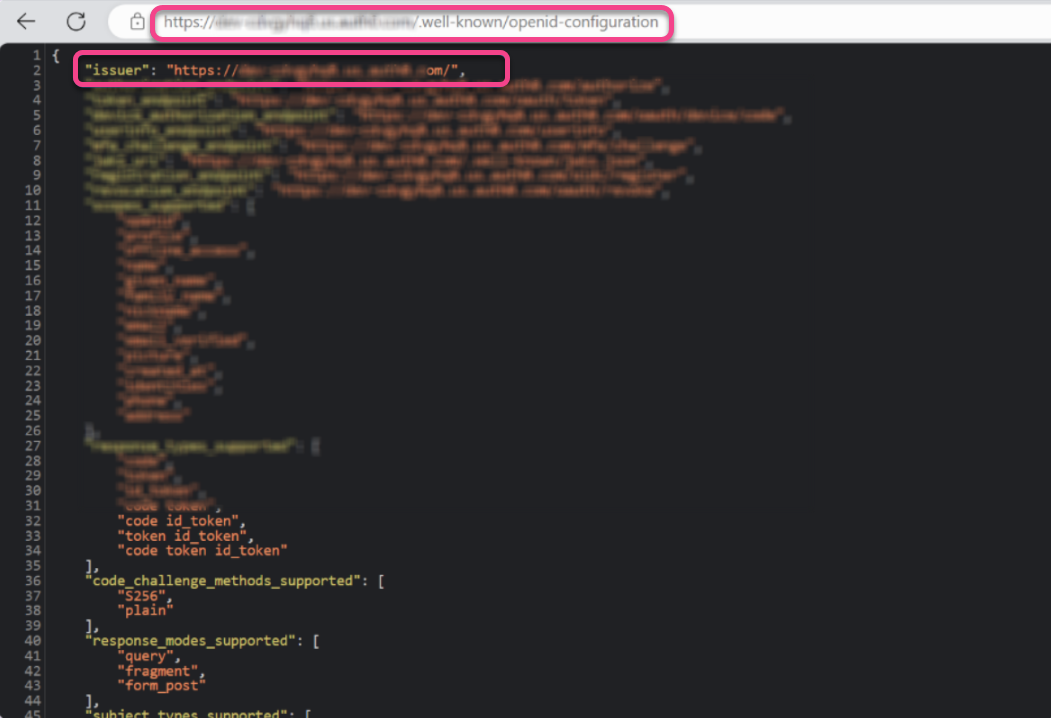
Access the discovery document specific to your Identity Provider (IdP) by using the following URL format:
https://<domain>/.well-known/openid-configurationFor example, if you're using Auth0, it might look like:
https://your-domain.auth0.com/.well-known/openid-configurationOpen this URL in a web browser to view the discovery document.
Retrieve and update the Authority URL in Document360
In the discovery document, locate the field labeled
"issuer".Copy the value of this field; this is your correct Authority URL.
Log in to your Document360 project.
Navigate to Settings () > Users & permissions > SSO Configuration.
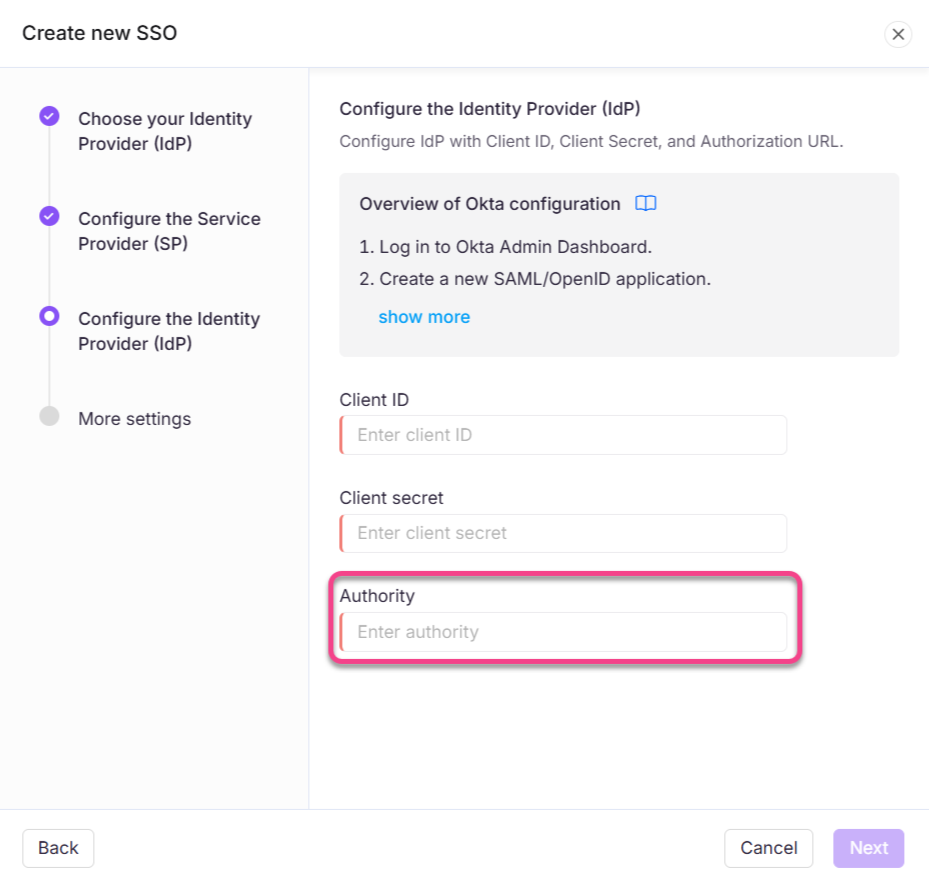
Click Edit on your existing OpenID SSO configuration and navigate to the Configure the Identity Provider (IdP) page.
In the Authority field, paste the copied URL.
Verify and test the configuration
Ensure there are no trailing spaces or incorrect characters in the Authority URL.
Save the configuration.
Attempt to log in using SSO to verify that the issue is resolved.
If the problem persists after following these steps, consider checking for network issues or firewall settings that might block access to the Identity Provider's configuration endpoint. Additionally, ensure that your Identity Provider's SSL certificates are valid and not expired, as this can also cause connectivity issues.