Plans supporting this feature: Enterprise
You can configure Document360's SAML Single Sign-On (SSO) with the Microsoft Entra as the Identity provider. Please note that only users with Owner or Admin as Project role can configure SSO in Document360.
PRO TIP
It is recommended to open Document360 and Entra in two separate tabs/browser windows, since configuring SSO in Document360 will require you to switch between Okta and Document360 multiple times.
Adding an application in the Azure portal
Accessing the Azure AD portal
Log in to your Microsoft Azure account.
Click on Portal available on the top-right of the panel.
You would be redirected to the portal (Link: https://portal.azure.com/#home).
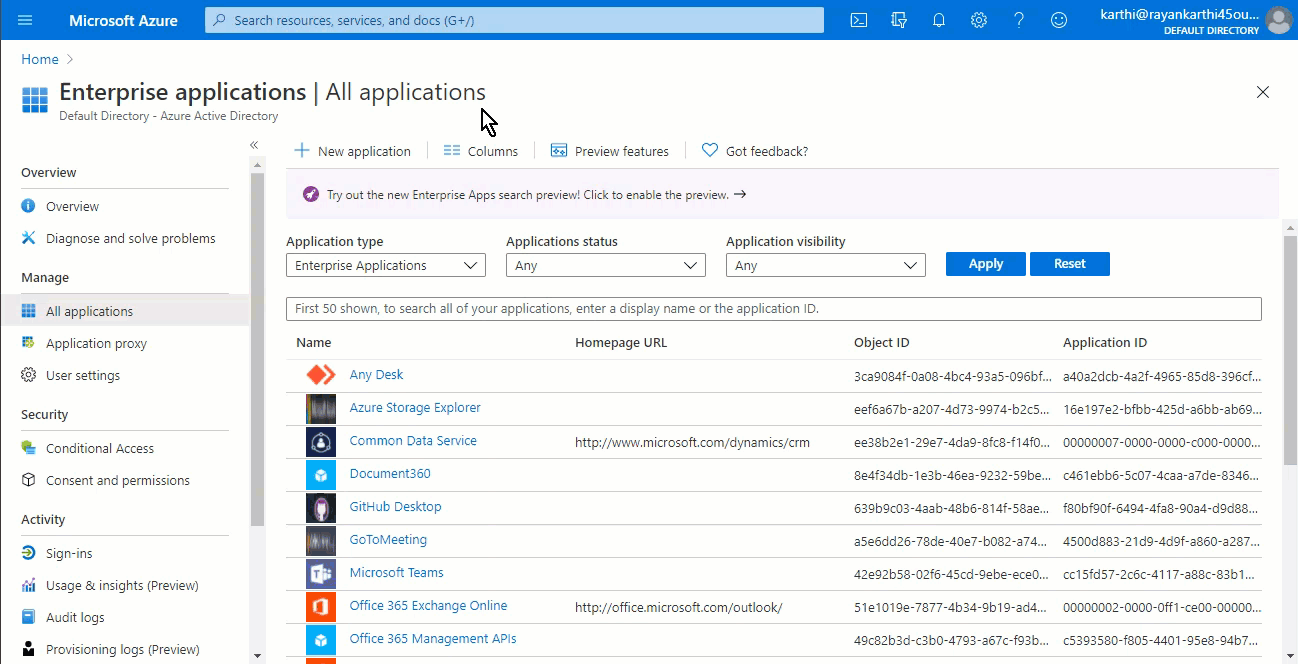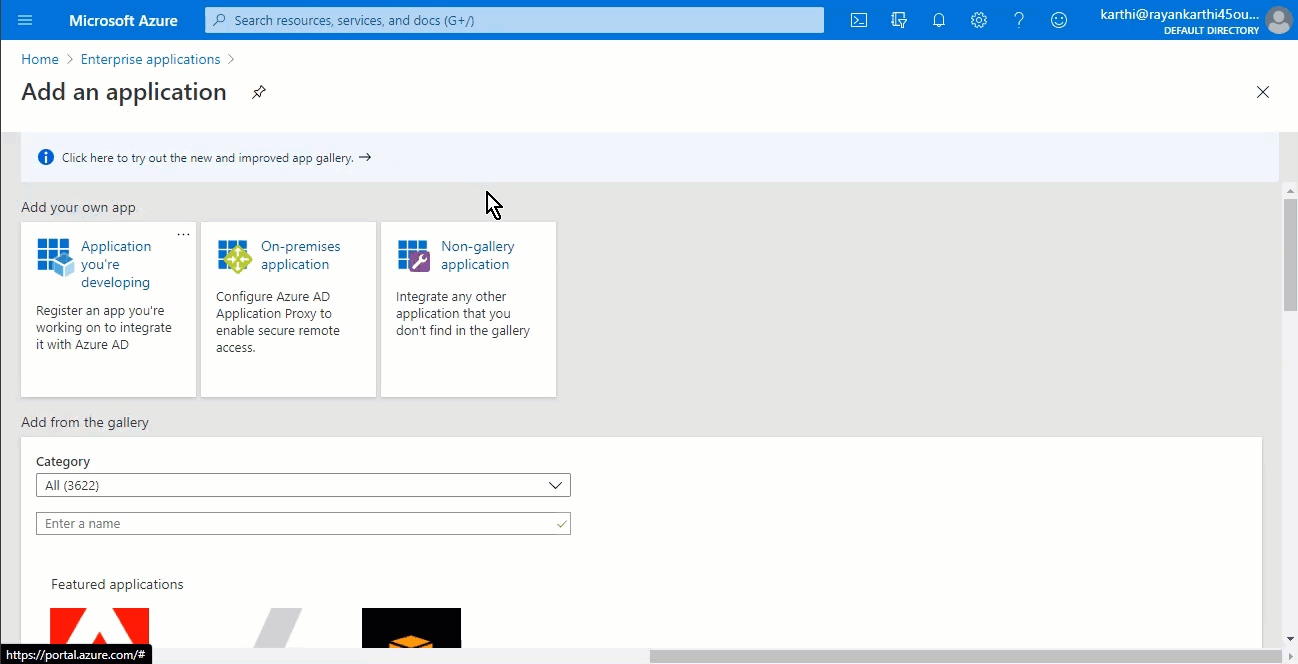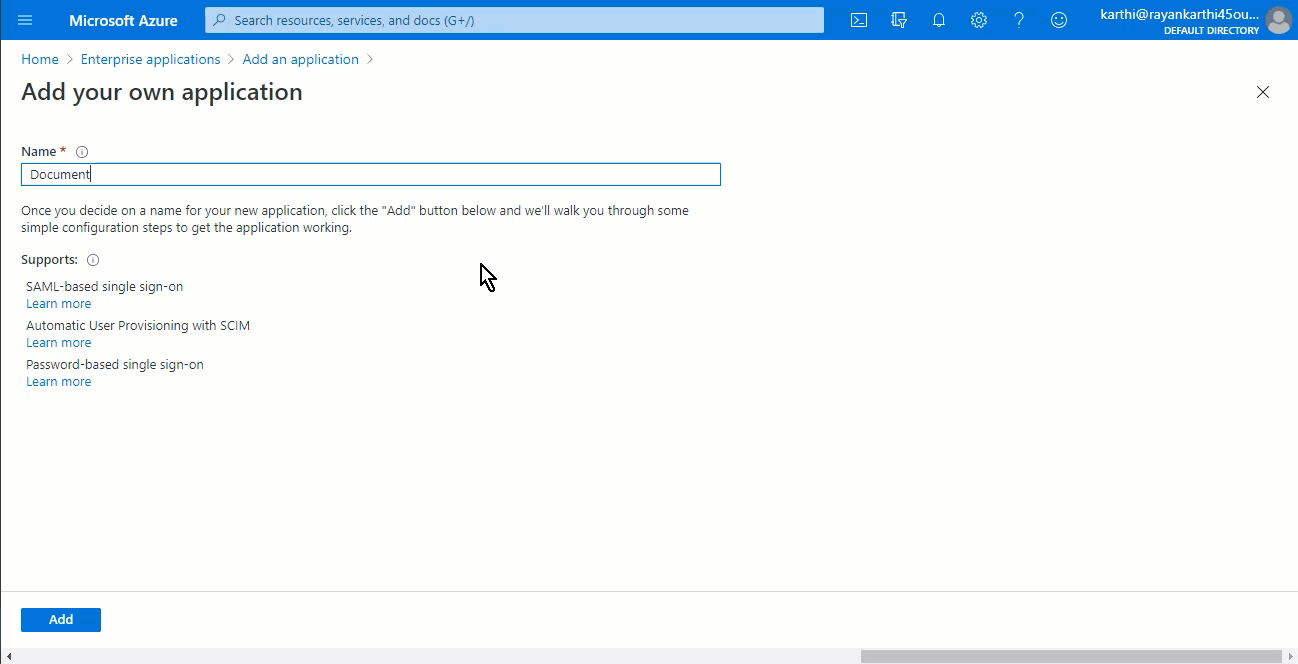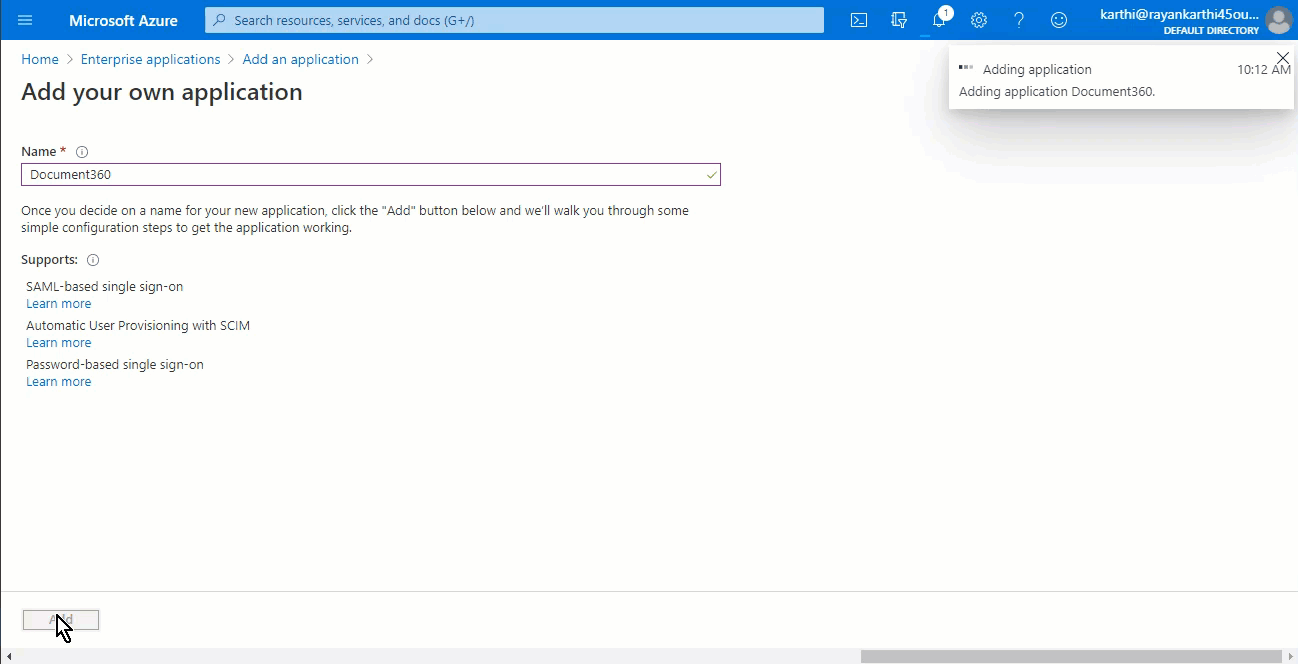
Adding your application
The 'Own application' is called 'Customer application' in this document.
Log in to your Azure account and visit the Azure portal page.
From here click on the + New application option and select Non-gallery application.
Type in the name of your application and click on the Add button at the bottom.
Now you would get a panel with the Project name, Application ID, and the Project ID.
In the Getting started section, select the Set up single on option.
These are the three selections provided
SAML
Password-based
Linked SSO
Select the SAML option, and you can find the five segregated SAML configurations.
You can read a detailed walkthrough of the process in the Azure AD configuration guide.
Configuring SAML in your identity provider
Open Document360 in a separate tab or panel.
Navigate to Settings > Users & permissions > SSO Configuration in Document360.
Click the Create SSO button.
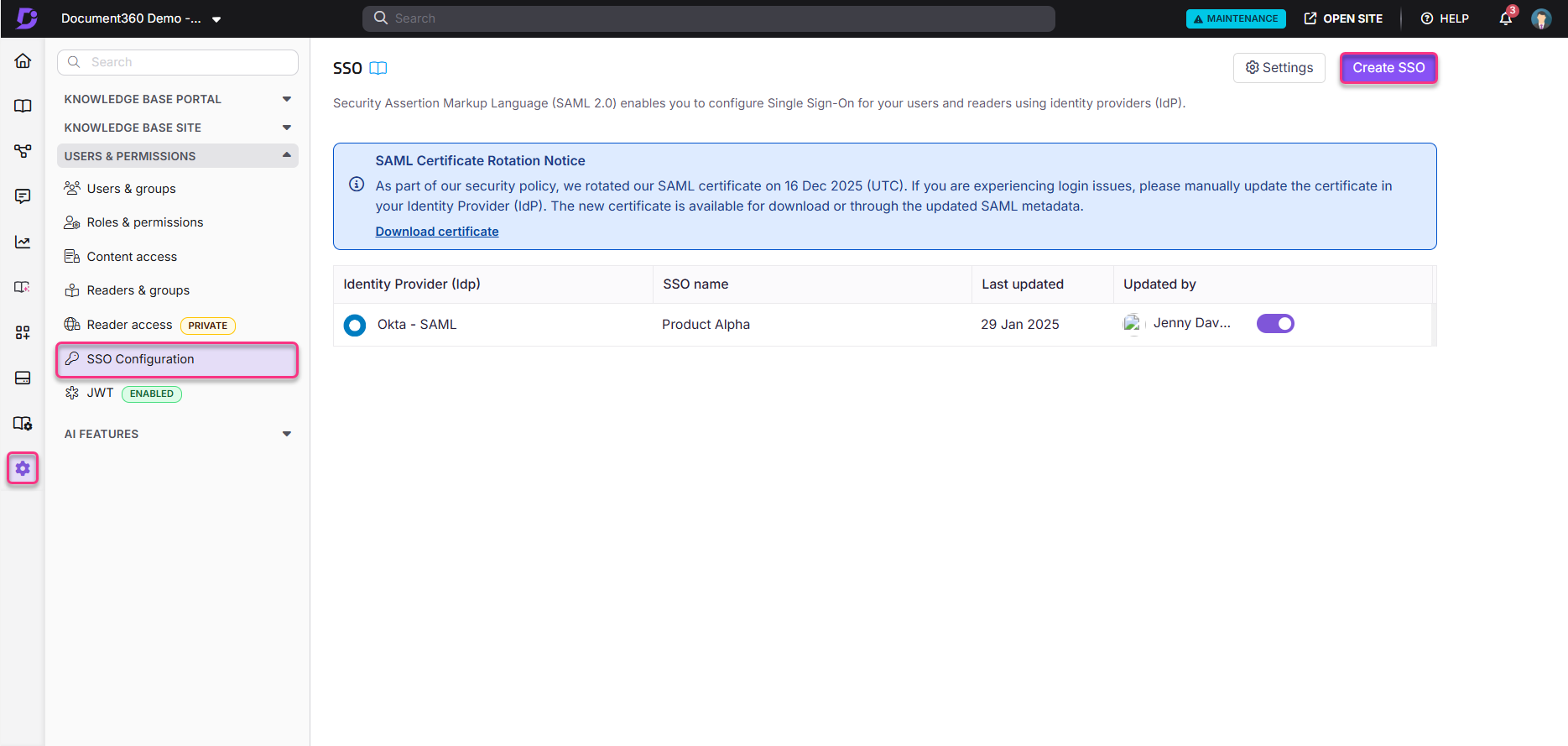
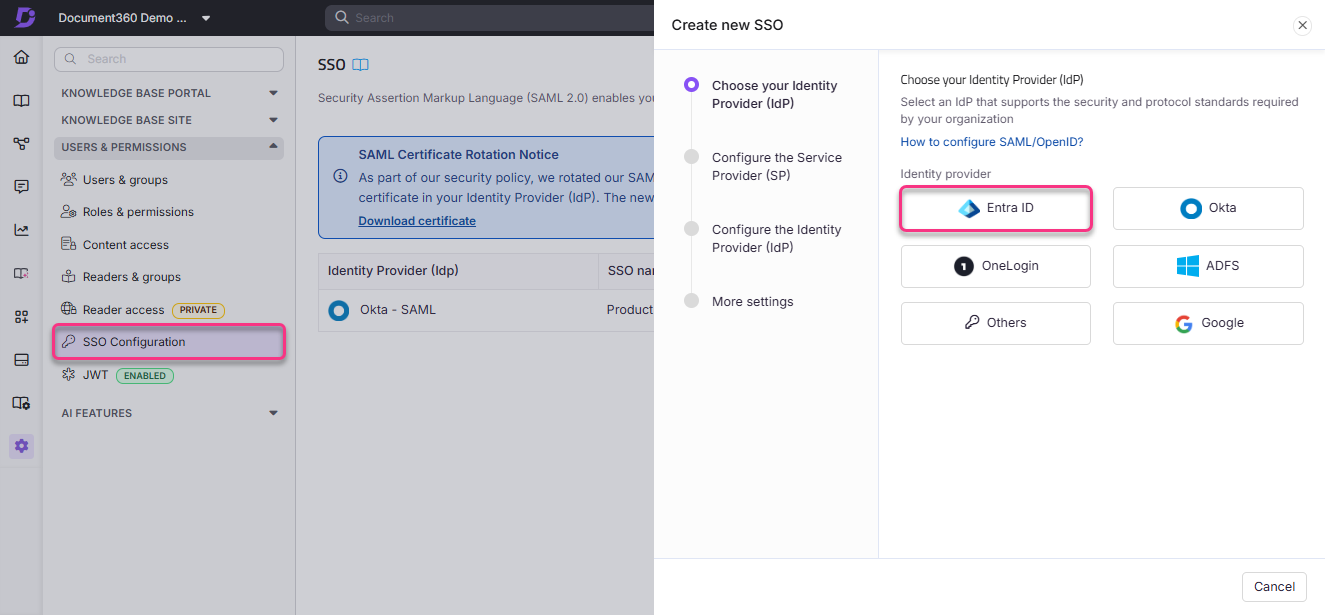
Select Entra ID as your Identity Provider (IdP) to navigate to the Configure the Service Provider (SP) page automatically.
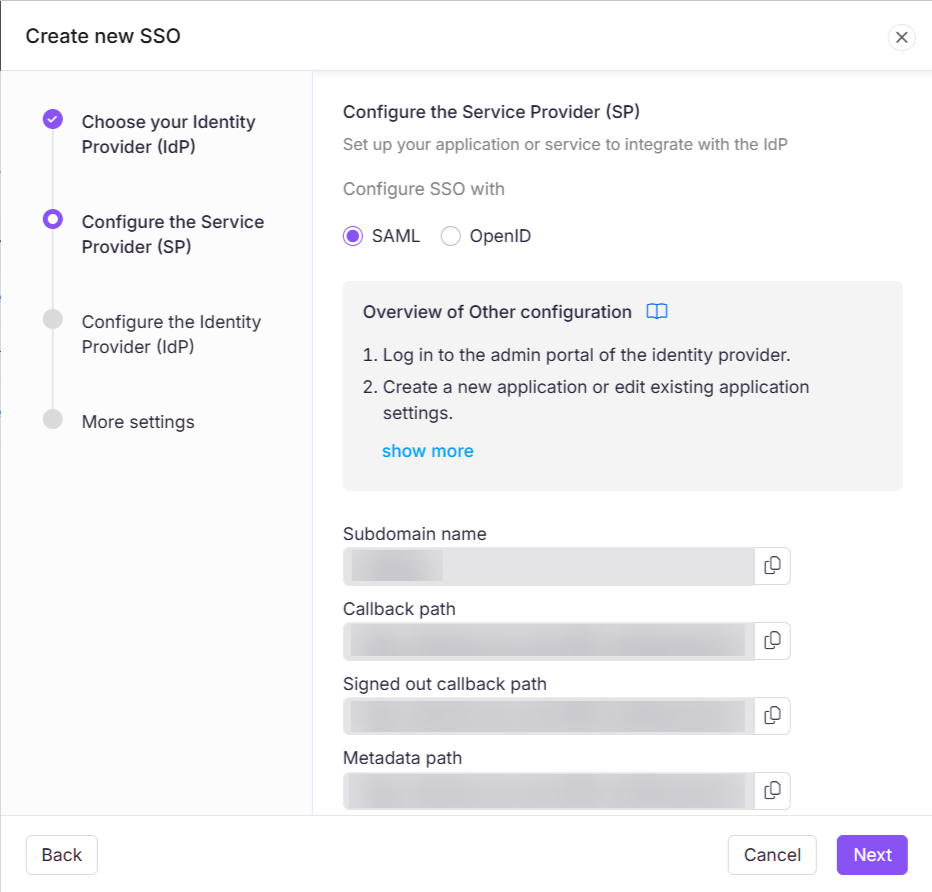
In the Configure the Service Provider (SP) page, you'll find the required parameters to configure your SAML integration in the Identity Provider.
Azure AD fields | Document360 portal |
|---|---|
Identifier (Entity ID) | Service provider entity id |
Reply URL (Assertion Consumer Service URL) | Callback path |
Sign on URL | https://identity.document360.io (the login page) |
Logout URL | Signed out callback path |
Copy these from Document360, switch to the Azure AD portal.
On the Set up Sign-On with SAML page, click the Edit icon on the right and paste the data in the corresponding fields defined in the above table.
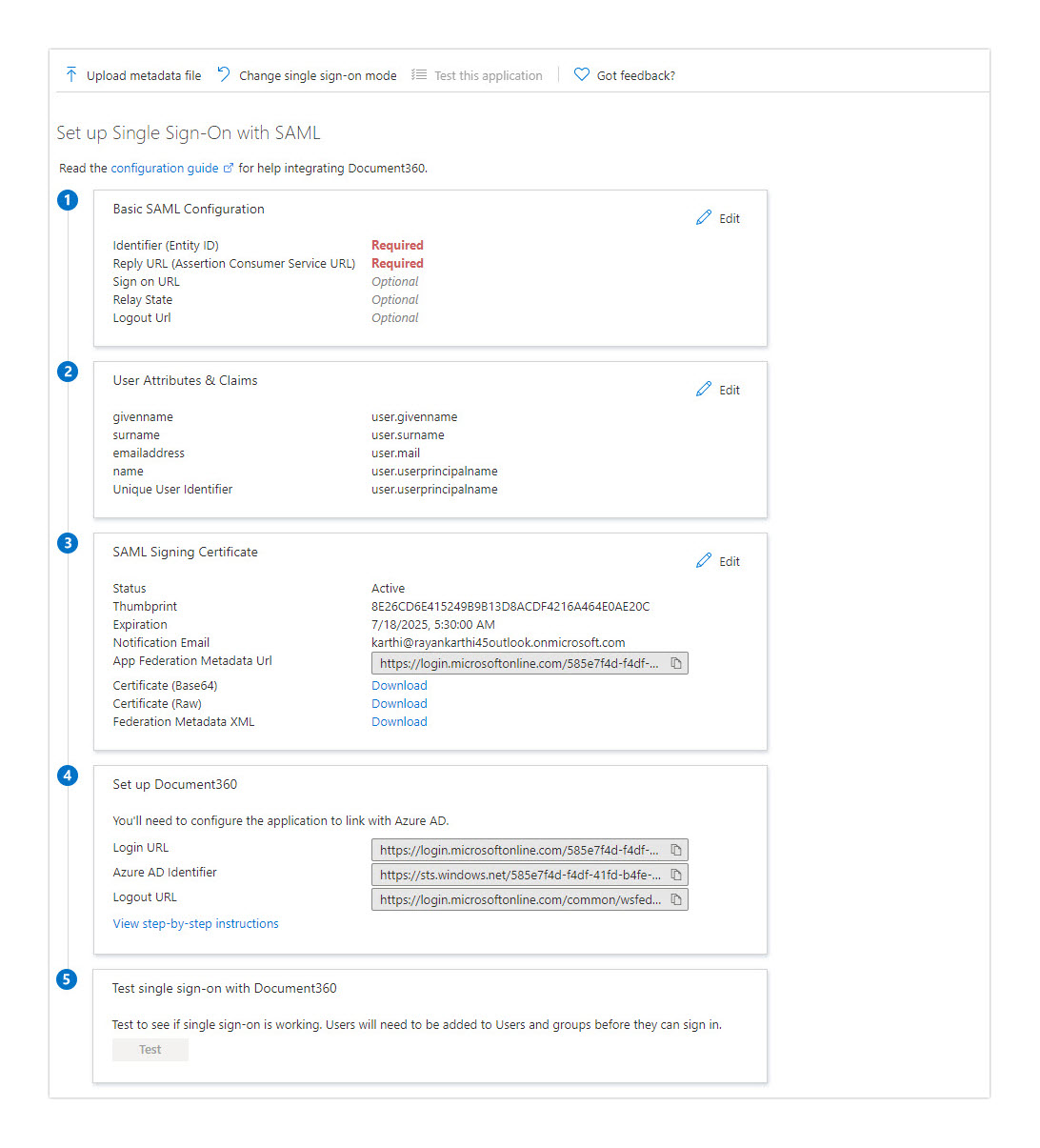
Click on the Save icon at the top after you've entered all the mandatory fields
Document360 SSO configuration
Finally, complete the SSO configuration in Document360:
Return to the Document360 tab/panel displaying the Configure the Service Provider (SP) page and click Next to navigate to the Configure the Identity Provider (IdP) page.
Enter the corresponding values from your Identity Provider:
Document360 portal fields | Azure AD portal values |
|---|---|
Sign On URL | Login URL |
Entity ID | Azure AD identifier |
Sign Out URL | Logout URL |
SAML certificate | Download Certificate (Base64) from Azure AD side and upload in Document360 |
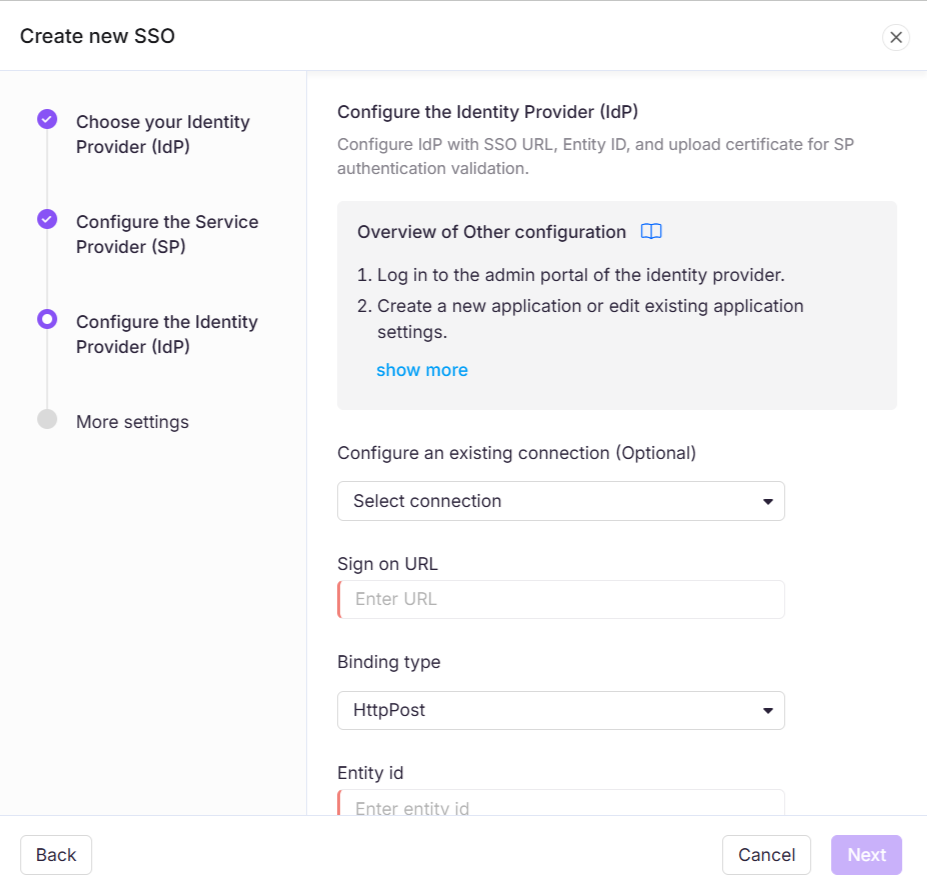
Toggle on/off the Allow IdP initiated sign in option based on your project requirements.
Click Next to proceed to the More settings page.
More Settings
In the More settings page, configure the following:
SSO name: Enter a name for the SSO configuration.
Customize login button: Enter the text for the login button displayed to users.
Auto assign reader group: Toggle on/off as needed.
Sign out idle SSO user: Toggle on/off based on your requirements.
Choose whether to invite existing user and reader accounts to SSO.
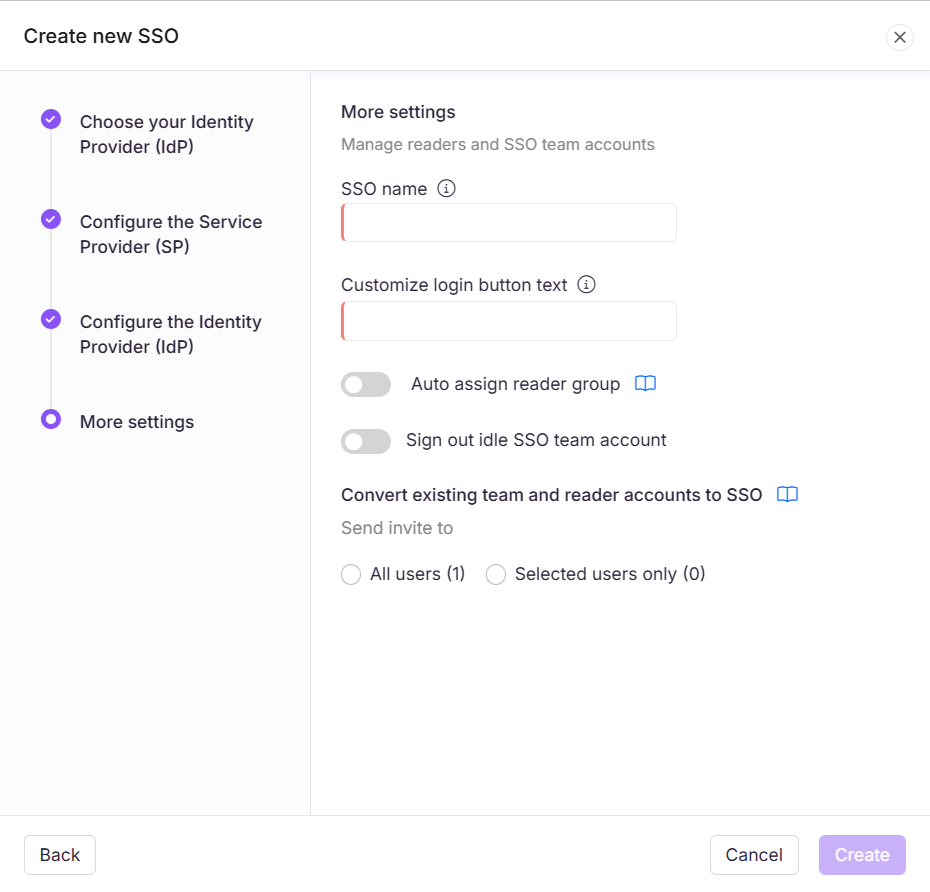
Click Create to complete the SSO configuration.
Other configuration settings in the Azure AD portal
You can always edit the User Attributes & Claims section
You can either Add a new claim or Add a group claim as well
In the SAML signing certificate section, you can add New certificates or even Import certificates
Multiple notification email addresses can also be added
Once all the fields have been configured, click on the Test option and Log to Document360 using the credentials the user has added to the registered application