Plans supporting this feature: Enterprise
SAML 2.0 is an open standard protocol that allows users to access multiple web-based applications with a single set of credentials. This provides a more secure and convenient way for users to access Document360. With SAML 2.0 enabled, Document360 users can log in to the platform using their existing credentials from an identity provider (IdP). Document360 supports the configuration of multiple single sign-on (SSO) endpoints, allowing both users and readers to log in using their preferred identity provider.
Supported identity providers
Document360 supports the following identity providers (IdP):
Okta
Entra ID
Google
Auth0
ADFS
OneLogin
Others
Configuring SSO using SAML
Log in to your Document360 account and navigate to your desired project.
Navigate to Settings () > Users & permissions > SSO Configuration.
Click Create SSO.
Select an identity provider from the Choose your Identity Provider (IdP) page.
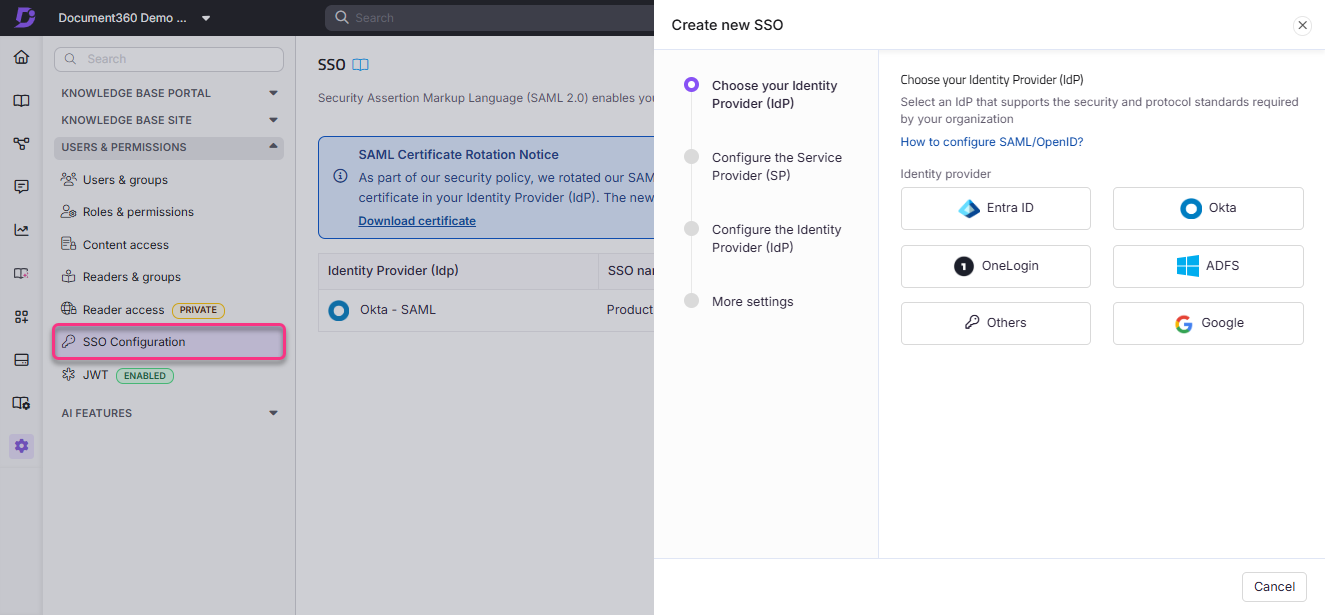
Select SAML from the Configure the Service Provider (SP) page.
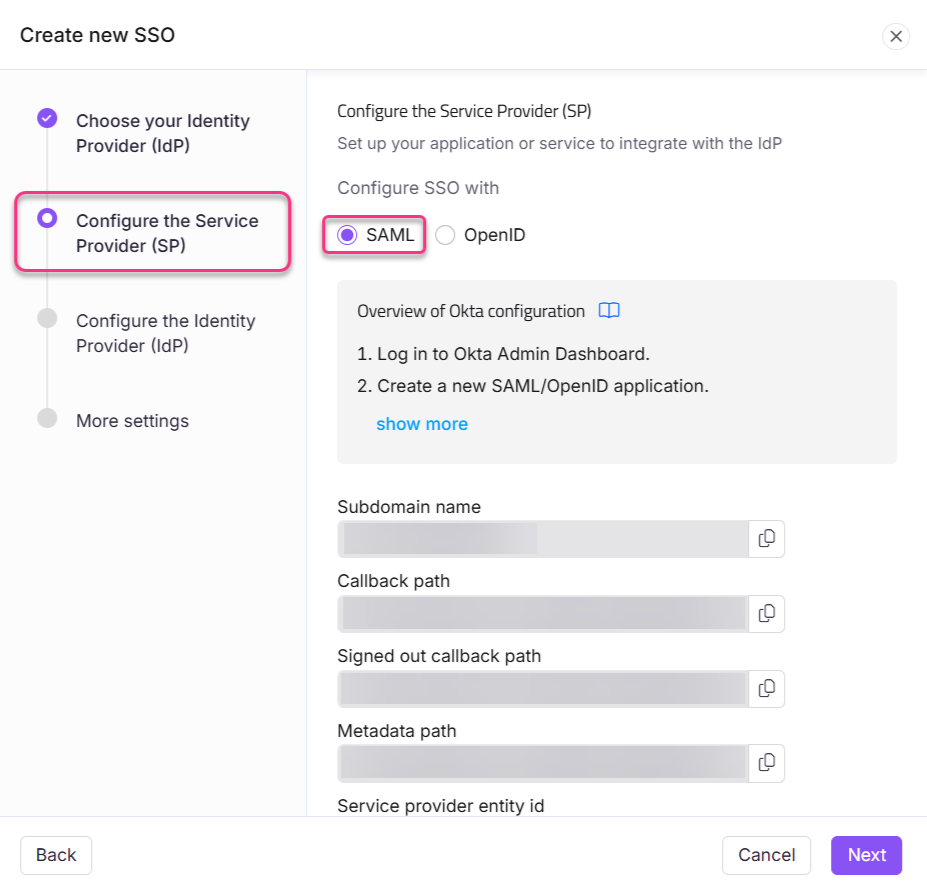
Using the details provided in the Configure the Service Provider (SP) page, configure the Document360 application with the previously selected identity provider.
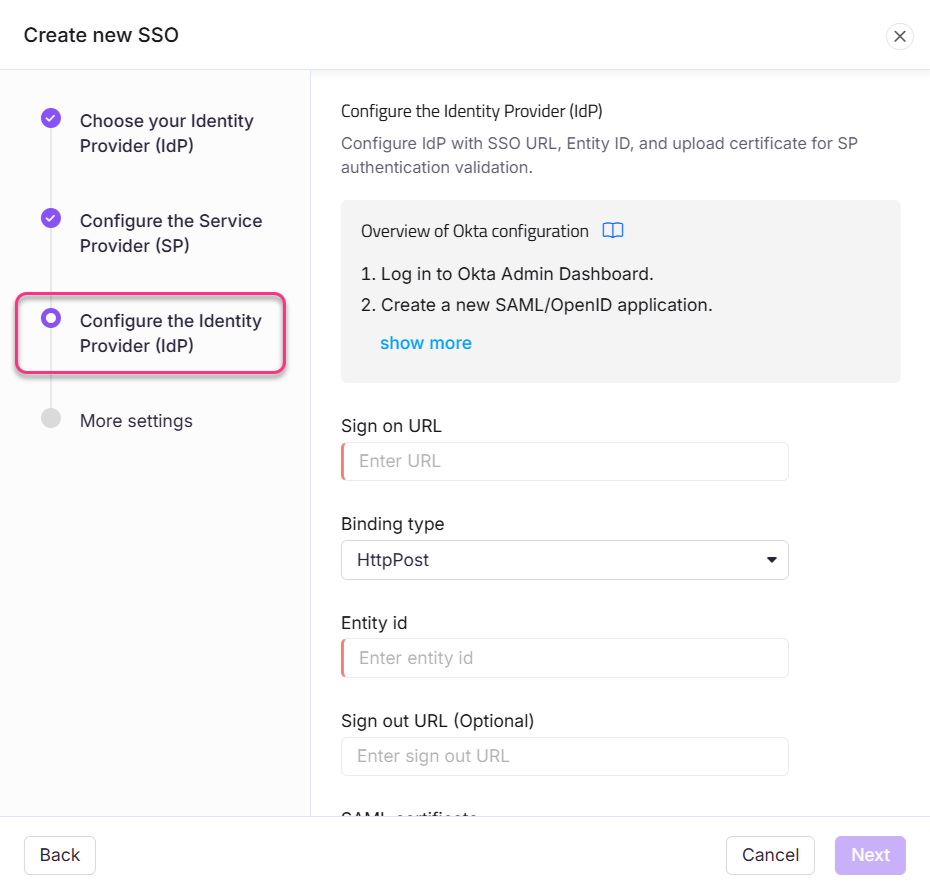
Using the details provided by the identity provider, setup the SSO configuration in Document360 on the Configure the Identity Provider (IdP) page.
Enabling direct Knowledge base site redirection (IdP-initiated SSO)
If you want users signing in through an IdP-initiated SSO flow to be redirected directly to your Knowledge base site (instead of the Project dashboard), you must configure the RelayState parameter in your Identity Provider (IdP).
To configure this:
Log in to your Identity Provider (IdP) admin console (for example, Okta, Entra ID, Auth0, or ADFS).
Open the SAML application you created for Document360.
Locate the RelayState (or equivalent) field.
Enter the URL of your Knowledge base site.
For example:
https://docs.yourdomain.comSave your configuration.
Test the IdP-initiated login to verify that users are redirected directly to the Knowledge base site.
NOTE
If the RelayState field is left blank, users will be redirected to the Document360 Project dashboard by default.
Once you have successfully completed the SSO configuration based on the SAML protocol, you can invite members from your project to the configured SSO application.
Now, users can login to Document360 either using their email and password or using SSO.
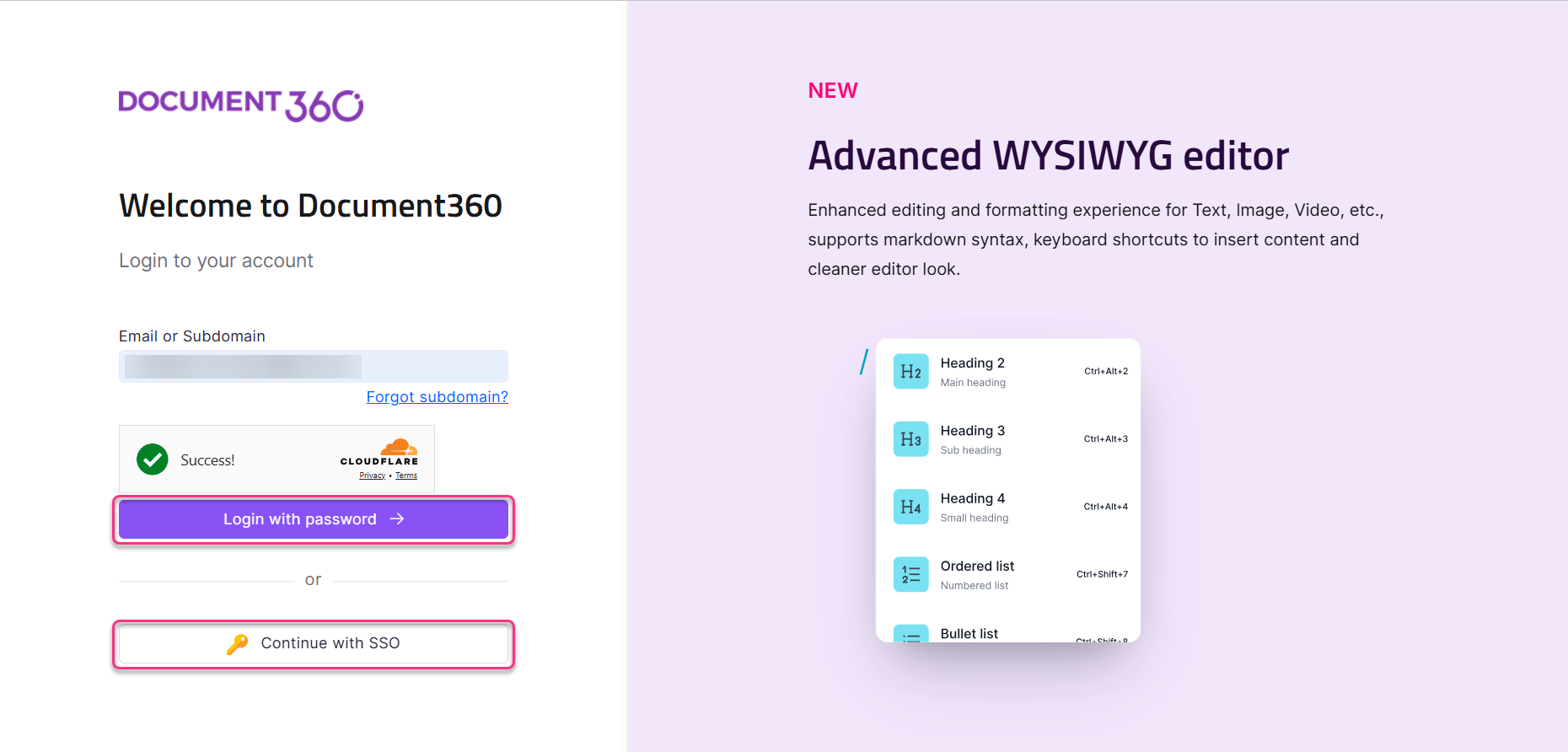
Troubleshooting
If you encounter issues during the SAML SSO setup or login, refer to the following common errors and their solutions:
Invalid SAML request (Untrusted key)
Error: An error was encountered while handling the remote login - Invalid SAML Request SAML signature is valid but uses an untrusted key. This error occurs when the SAML certificate uploaded to Document360 is inactive.
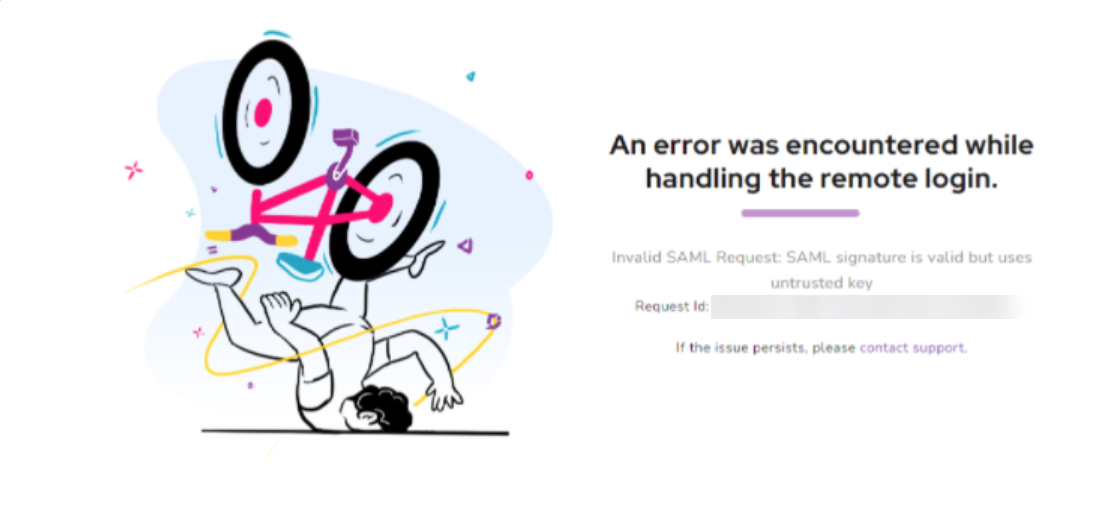
Steps to resolve:
To resolve this issue,
Download the active SAML certificate
Access your IdP.
Download the currently active SAML certificate.
Re-upload the certificate in Document360
In Document360, navigate to Settings () > Users & permissions > SAML/OpenID.
Click Edit for the relevant SSO configuration.
Under Configure the Identity Provider (IdP) section, locate the SAML Certificate field.
Click Browse to upload the new, active certificate.
Uploading the active certificate should resolve the issue.
SAML message signature is invalid
Error:
SignatureInvalid: SAML message signature is invalid.
AssertionSignatureInvalid: SAML Assertion signature is invalid.
Invalid SAML Request: SAML signature is valid but uses an untrusted key.
This error occurs when an incorrect or expired SAML certificate is uploaded to Document360.
Steps to resolve:
Ensure the certificate is valid:
Check if the uploaded certificate is active and not expired.
If needed, generate a new certificate in the Identity Provider (IdP).
Re-upload the correct certificate in Document360:
In Document360, navigate to Settings () > Users & permissions > SAML/OpenID.
Click Edit for the relevant SSO configuration.
Under Configure the Identity Provider (IdP) section, locate the SAML Certificate field.
Click Browse to upload the new, active certificate.
Capture Logs for Further Analysis (if issue persists)
Add the SAML Tracer extension to your browser.
Open SAML Tracer before starting the SSO login flow.
Perform the action that triggers the SSO process (e.g., clicking Continue with SSO).
SAML Tracer will record all network requests.
Right-click in the SAML Tracer panel.
Select Export or save the logs in a suitable format.
For further assistance, contact the Document360 support team with:
Screenshots of your IdP configuration.
The uploaded SAML certificate details.
SAML Tracer logs.
FAQ
Can I change the subdomain name in the SSO configuration?
No, the subdomain name cannot be changed once it is configured. The field will appear greyed out to indicate that it is not editable.
Can I create multiple SSO (IDP) configurations with the same name?
No, each IDP (Identity Provider) configuration must have a unique name. Duplicate names are not allowed when creating multiple configurations.
Can I use the same display name (button label) for different SSO configurations?
Yes, while the internal IDP name must be unique, you can assign the same name to the login button that is visible to end users on the login screen.
How can I view the expiry of the Document360 SSO certificate?
You can see the expiry date of the Document360 SSO certificate (used for SAML authentication) from Settings > Users & permissions > SSO Configuration.
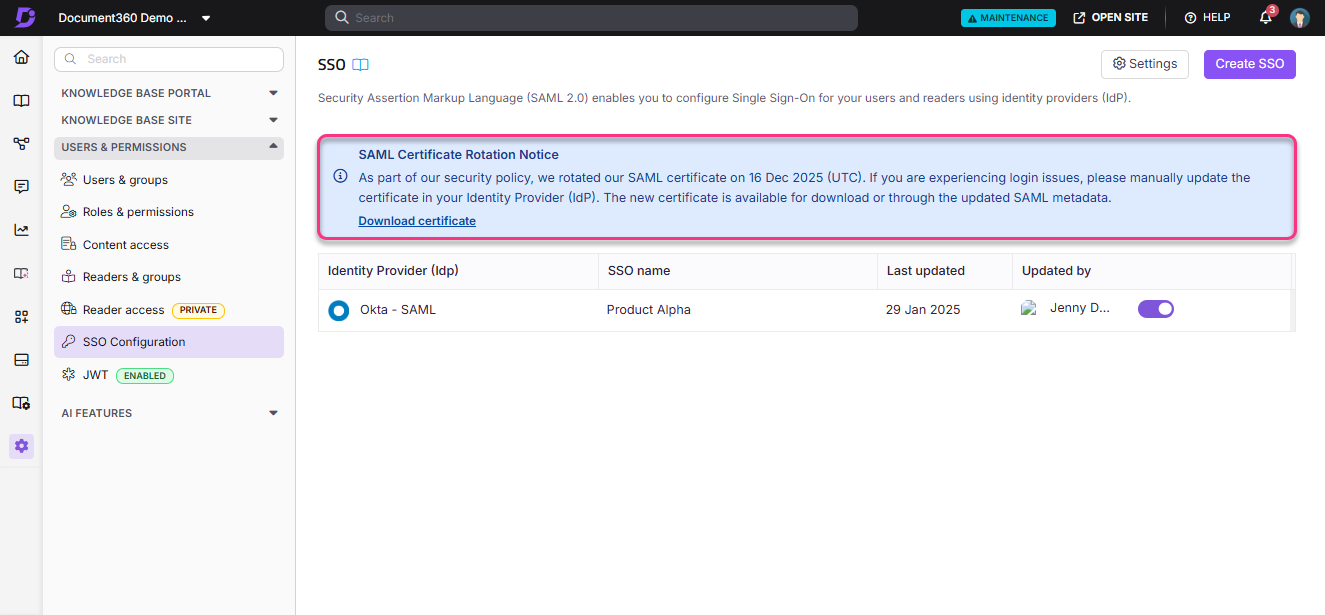
A blue information banner appears above the SAML configuration list 15 days before the certificate expires. This banner is visible only to users with permissions to configure SSO.
How can I download the Document360 SSO certificate?
You can download the Document360 SSO certificate directly from the blue banner displayed on the SAML/OpenID page. Click Download certificate in the information banner to download the certificate in .cert format.
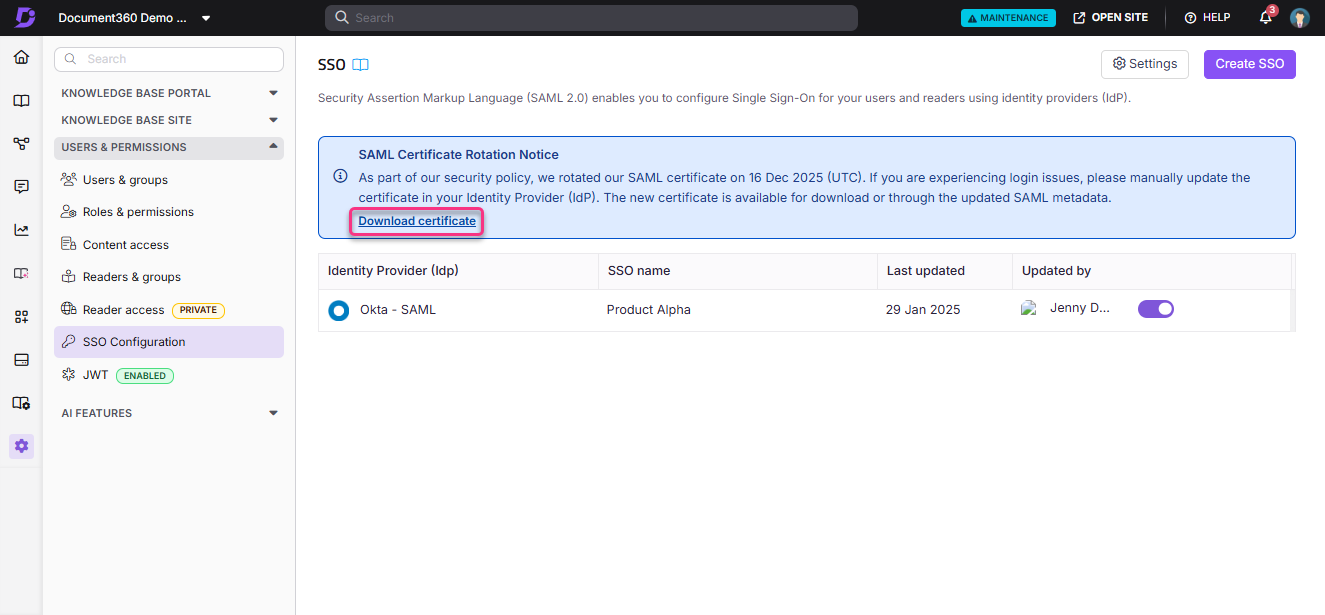
This certificate is required when renewing SSO in your Identity Provider (IdP), especially for IdPs that cannot read the certificate automatically from metadata.
NOTE
Downloading the Document360 certificate does not affect your existing SSO configuration. It is needed only when renewing the certificate on your IdP.